Back in July of 2019, Delinea released DevOps Secrets Vault, a high-velocity vault for high-speed password and Secret creation, archiving, and retrieval. Each month we roll out improvements to this cloud-based tool. In 2020, we’ve been focused on adding dynamic secrets for key cloud platforms.
For infrastructure-as-a-service platforms dynamic secrets in DevOps Secrets Vault offer another layer of security
The foundational idea behind a vault specifically for DevOps tools is to replace hard-coded credentials, passwords, and multiple disparate vaults with an API call to a centralized location where secrets are encrypted, access is controlled, and auditing is provided. Of course, the DevOps tools only use the secrets to do what they need to, but can you trust them not to leak the secrets themselves? For infrastructure-as-a-service (IaaS) platforms, such as Amazon Web Services (AWS), Microsoft Azure (Azure), and Google Cloud Platform (GCP), dynamic secrets in DevOps Secrets Vault offer another layer of security.
Whether some or all your infrastructure is in the cloud, the impact of lost or stolen passwords or secrets could range from temporary disruptions to critical data loss. DevOps tools from Jenkins to Terraform to Ansible all have open-source and commercial pieces to them, numerous plug-ins to other tools, and library dependencies. All of this makes them very powerful, but along the way, there could be vulnerabilities or misconfigurations that leak secrets. This can happen when secrets are improperly stored in memory or on disk, sent to logging systems, or leaked to other tools or processes.
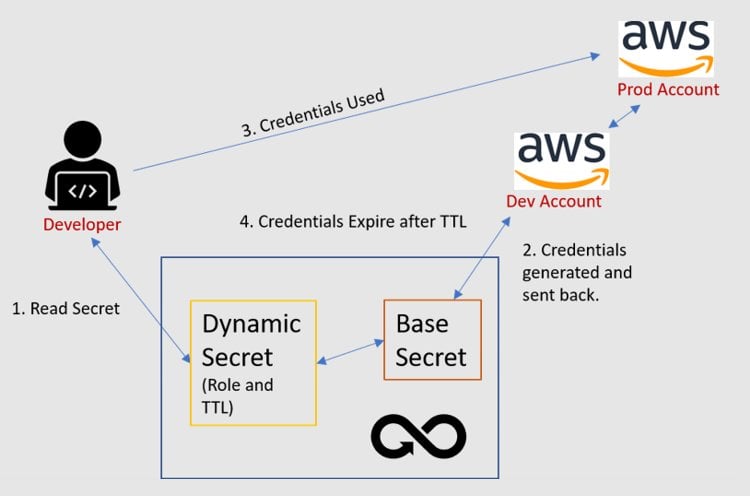
Dynamic secrets (aka dynamic passwords or ephemeral secrets) eliminate the problem with these potential leaks because they are created only when needed and then expire. When the DevOps tool needs to perform its function and accesses the Secret, a new one is generated. Dynamic secrets also enable fine-grained authorization through cloud policies. Limiting the authorization scope and timeframe greatly reduces and even eliminates any value of the Secret to an attacker.
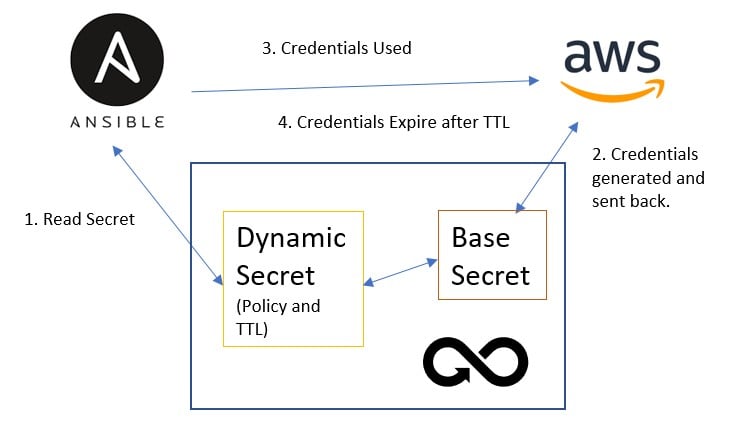
Here is an illustration of how dynamic secrets work in an environment with Ansible, AWS, and DevOps Secrets Vault: