Why the right vault is critical to Extended PAM
Humans are the weakest link in IT security and yet organizations consistently allow overprivileged users, human and machine, to exist and run wild across privileged accounts.
Protecting business-critical digital assets is more complicated as environments become more complex and widely distributed across identities, locations, and networks. Adding to your plate dealing with evolving cybercriminal networks and their increasingly sophisticated, targeted attacks makes it extremely difficult to protect privileged accounts for any organization.
As a result, IT and Security leaders are evaluating their current PAM security structure from the ground up to ensure they are investing in the right tools to protect the organization and their team.
The exploding number of identities needed to be managed is forcing PAM security tools to evolve. IT and security leaders who have little visibility when managing privileged accounts and identities with access across multiple applications put organizations in a dangerous predicament. Extending PAM security across the entire IT infrastructure can solve this security vulnerability.
IT and Security leaders make their organizations much more vulnerable to a breach by lacking a full understanding of:
- Privileged identities
- The complete landscape of vulnerability
- How privileged accounts function
- Risks associated with compromised credentials and misuse
The absence of a comprehensive Privileged Access Management (PAM) solution across your entire organization inevitably increases security gaps.
What is Extended PAM?
Extended PAM is all about understanding access, specifically who and what in your organization needs access, then establishing when and where the necessary controls to elevate access are needed. Extended PAM provides the ability to adapt to risk based on user behaviors observed throughout the organization.
Extended PAM reduces the attack surface across your entire enterprise by treating all users as privileged users with appropriate parameters and controls in place for human and non-human users. In short, all users are treated as privileged users. Teams across organizations will all reap the benefits of Extended PAM, including DevOps, Cloud infrastructure, Remote Work, and SaaS.
Related reading: Extended PAM: Intelligent automation for risk-based, adaptive privilege
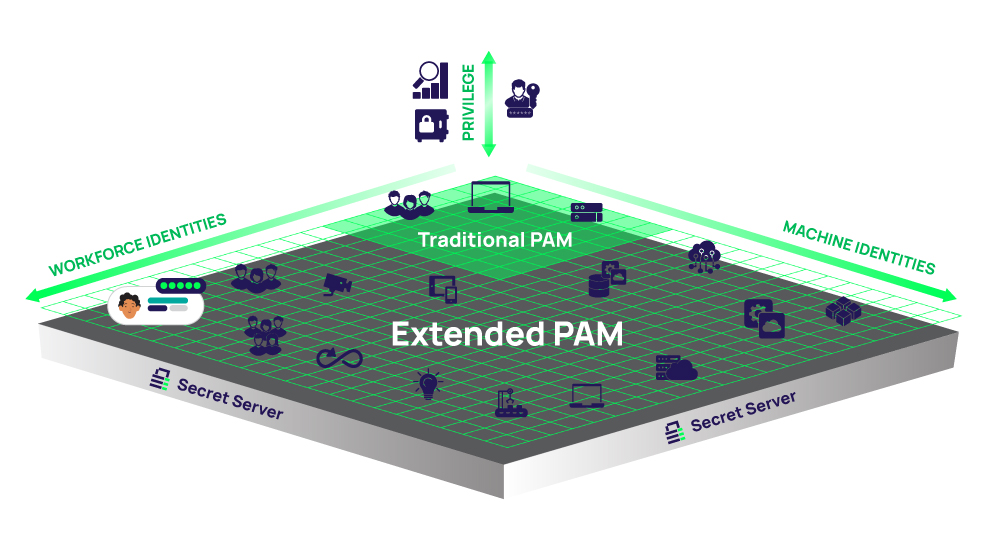 Extended PAM at a glance
Extended PAM at a glance
Set a solid foundation
The journey to extending PAM security begins with a proper vault that seamlessly protects privilege as you scale.
The primary target of advanced attacks is to steal or simply gain access to credentials. By gaining access to these credentials, attackers can then hijack unmanaged, unmonitored, or poorly protected privileged accounts. A modern, easy-to-adopt enterprise PAM vault with the appropriate robust feature set mitigates risk and sets the foundation for adoptable user-friendly security processes that scale.
At least 80% of data breaches have a connection to compromised privileged credentials, such as passwords, tokens, keys, and certificates ~ 2022 Verizon DBIR. Check out the Key Takeaways from the Verizon Data Breach Investigations Report 2022
Without the right vault, unauthorized access can go undetected for months, allowing attackers to run advanced persistent attacks
Let’s not forget over-privileged third-party vendors, a growing concern as organizations outsource more projects to scale quickly. Once credentials are accessed by bad actors, the permissions are escalated to gain access to more privileged accounts. Without the right vault, this unauthorized access can easily go undetected for weeks or even months, allowing attackers to run advanced persistent attacks to see and steal information at their convenience.
It’s critical to identify and adopt an easy-to-use secure vault that fits your environment and provides insight into ALL privileged users, including vendors.
Organizations must confidently identify, manage, and protect these privileged accounts before extending privileged management across the entire organization. This is why the vault is foundational to extending PAM security – authorization for each privileged user starts here.
A PAM vault is an investment
A feature-rich PAM vault should be viewed as an investment in an organization’s future. The right vault supports the least standing privilege mindset of PAM security everywhere, with seamless adoption across users and secure access controls.
The right vault positions organizations to secure privileged credentials properly, continuously discover privileged accounts as you scale, seamlessly add automation to do more with less, and simplify proof of compliance. The proper vault should be connected to long-term business goals, providing key functionality that frees the IT team to focus on business-critical projects. At the same time, having the appropriate vault mitigates risk for the entire organization.
According to Gartner, “The accelerated migration to the cloud, the blurring of enterprise security perimeters, and the overall increase in the number of cyberattacks all contribute to the growth of PAM adoption.”
Extended PAM, built on a secure vault, allows you to address the increasing expansion and vulnerabilities of all privileged access
Modern tools for PAM must support numerous requirements to be effective, from protecting the passwords of shared accounts, to rotating the passwords of service and system accounts while securely managing remote access tunnels. PAM tools must also be scalable to encompass the ever-expanding privileged account attack surface. It’s mission-critical to the team’s productivity to manage the exploding number of identities, human and machine, across the IT infrastructure with automation. It all starts with the right foundational vault.
Extended PAM, built on a modern, secure vault, allows you to continue incorporating capabilities to address the increasing expansion and vulnerabilities of all privileged access.
Read more in the 2022 Gartner® Magic Quadrant™ for Privileged Access Management
Evolve your expectations
It's essential to understand that extending PAM across your IT infrastructure begins with a vault that does more than just secure privileged credentials. It needs to also enable IT teams to do more with less, all while contributing to the organization’s business goals.
An effective and efficient PAM vault reduces an organization’s attack surface, mitigating risks regardless of their IT infrastructure and environment. As the goal of existing password vaulting and session management technologies continues to mature, IT and security teams must evolve their strategy simultaneously.
Extended PAM, built on a modern, secure vault, allows you to continue incorporating capabilities to address the increasing expansion and vulnerabilities of all privileged access. Doing this with a mindset focused on continual growth and building up from the solid foundation set by the appropriate vault will make extending PAM across the organization much more seamless.
Learn more about the importance of the right PAM vault:
IT security should be easy. We'll show you how