How to Secure Machine Identities in an AI Environment
As non-human and machine identities like bots, APIs, and containers outnumber human users in your environment, challenges such as lack of governance, excessive access, and limited visibility put your organization at risk. Jeff Carpenter explains how to gain control by applying identity security best practices to machines—managing lifecycle, access, and ownership—while also securing the AI systems you use or build. Delinea helps you reduce risk and maintain accountability across your growing infrastructure.
Hello, I'm Jeff with Delinea, and let's talk about the rise of the machines and AI. Now, if you are like many organizations, what do you think the ratio of machines to actual carbon-based humans are in your environment? Well, some estimates are that right now we're looking at a 50 to one ratio, and of course climbing big time. So we're already outnumbered by the machines. And by machines we mean non-humans or non-human identities within our environment. And these are things like service accounts, containers, APIs, bots, like a chatbot for example, that are operating already within our environment and we're outnumbered.
And the idea is that how do we get our arms around the situation where we have all these machine identities out there? What are the key challenges and [00:01:00] how do we respond to them? Let's go ahead and dive right in. So one of the challenges of machine identities is that there is no governance.
And by governance, no governance here, we mean lifecycle and governance. And what that means is that typically in the human based, carbon based world, when there's an identity like an employee starts at a new company, you have their birthright, right? So they join the organization and they're given a certain set of things that they can do that they're authorized to do.
And then as they proceed through their career, they get more. The entitlements and things they can do, and eventually when they leave the organization, all of that gets taken away in theory. But with machines, what happens is machines beget more machines. So virtual machine can create another virtual machine in the test farm, can fail over to another machine.
A database can back up to another part of [00:02:00] the organization. And so these machines are doing this on their own with very little oversight as to when that machine is created. It's usually given the rights that it inherited from the machine before it, without somebody saying, is that too much access?
Or do they have too much that they can do too much authorization? So we call that governance and life cycle, and there's very little of it there when it comes to machines. And the next is too much access. Very similar. So, we're on a rocket ship here of access and it is going up. And these, again, these machines, service accounts, containers, things like that, they have typically
a lot of access. Because in development environments, you give things a lot of access so that they can get their job done so you're not inhibiting things. And there's also, when it comes to access, there's very little ties to, Hey, who actually [00:03:00] owns this process? Or who actually owns this container?
Or, API bot service account. So understanding who has access to that so you can tie it back and. Have a human owner that says, oh yeah, we no longer need that virtual test bed. Go ahead and take it down. And in cloud environments, people are very reticent. IT is very hesitant to actually take these things away, even if they see that, Hey, you know, that machine has not been used in six months, let's take it down.
And, somebody's gonna come screaming to them. So, so that's one of the issues there as well. And then of course, discovery is always big, right? Where are machines? How many do I have? Who's using them and what do they have access for? Well, we don't know. because machines get built up, they get taken down they're what are called ephemeral.
So discovery is a huge part of this. Being able to discover and on an ongoing [00:04:00] basis, know what those machines are. Where they're at and what they're doing. And next and final thing that we see as a challenge here is ai. AI is creating lots of new machines. In another video, we talk about how Delinea addresses AI by both securing, using AI, securing identities of all types across the organization as well as securing AI systems that organizations are building, the agents and the models and the data within those. But for the purpose of our discussion today, machines and AI, we see a lot of AI creating more machines. So you have lots of chat bots and lots of instances of AI spinning up these things, and we need accountability.
So how does Delinea address this and what are the best practices here? Let's take these one by one. For governance, we approach machines and AI with an identity security perspective from an identity security [00:05:00] perspective. So in other words, we're not coming at it by scanning, doing network scans and doing endpoint security.
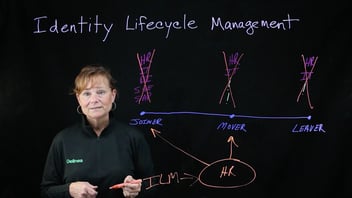
All that's great, but we're looking at it. As, hey, let's look at identity. What is this thing? What is it doing? Who gave it those rights and authorizations? And what is its ultimate lifecycle arc? And when can it be taken down and disabled? Who owns that? So Delinea addresses this with our identity lifecycle.
Delinea addresses this with our identity lifecycle management. So we treat machines like we do any other identity. And yes, you can assign owners to them. You can make sure that they don't have too much authorizations to do too much only what they need to do their job, and you can make sure that their access is secure.
Now, machines don't necessarily do multi-factor authentication. They have a variety of other authentication [00:06:00] methods, certificates, et cetera, that they use. But you can absolutely make sure that those machines are secure from other people accessing them, and they're secure with the connecting to the things that they need to get access to.
Next up is something Delinea does very well, and that is discovery. And discovery means that we go out and we use our technology, part of which is AI to scan. Scan your entire environment on-prem multi-cloud infrastructure to find these machine identities and to make sure you have at any one time a complete inventory of those machine identities, what they're connecting to their access pathways.
We actually have visualizers to show you how these machines got these machine identities, got the access they did, who gave them that, and we can trace back that graphically so that you make sure that you can pass audits [00:07:00] and what, where your most consequential machine identities are and what they're doing.
And finally, as we mentioned, AI, both securing AI, using it in our product, and also for your AI, whether you are using it as a service or whether you're building your own a AI models Delinea has you covered? Because we can secure those things, and you can see that in another video that we've created.
So this is how we secure machine identities and AI, 50 to one ratio go into a hundred to one. You need to get control of this as soon as possible. So check out Delinea.com for more information and thank you for watching this video.