Conversational Geek teaches you cyber insurance 101
If your business gets hit by a serious cyberattack, is it game over? Thanks to cyber insurance, this doesn’t have to be the case.
Cyber insurance, like auto or home insurance, reimburses the policyholder for losses incurred from a cyberattack. Sounds great, right? Well, the issue facing businesses looking to get cyber insurance is that cyber insurance is not a standard industry term, and there are countless policies and insurers. The key to navigating the cyber insurance labyrinth and getting the most appropriate coverage is preparation, organization, and knowledge.
To discover how cybersecurity and cyber insurance are intertwined, I’m pleased to introduce Conversational Cyber Insurance. In it, the experts at Conversational Geek break down the basics of cyber insurance and what to do when you are considering becoming a cyber insurance policyholder. This primer on the what, how, and why’s of business cyber insurance and will set you well on your way to understanding the complicated landscape of cyber insurance.
What is cyber insurance?
There are thousands of cyber insurance policies from companies around the world, with each insurer providing its own unique policy. Insurer offerings can range from industry-specific coverage options to improved coverage sub-limits.
Cybersecurity policies, as varied as they are, consist fundamentally of two “Sides”, four “Buckets”, and “Exclusions”, which are issues the policy does not cover.
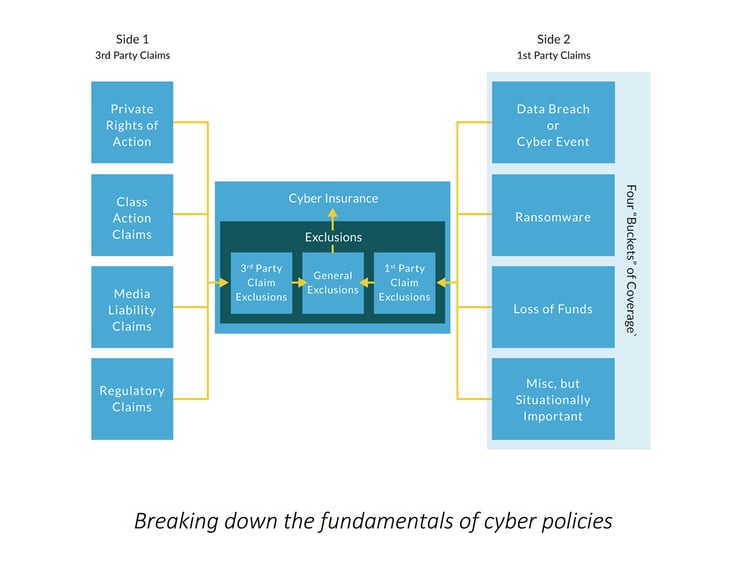
Side one: third-party claims
Third-party claims in a cyber insurance policy are claims brought against your business by clients, vendors, and payment card companies. After a cyber event occurs, third parties may bring a lawsuit against your business because they think they’ve incurred damages from the loss of your business services or identity theft. Suppose payment information was stolen and used fraudulently. In that case, payment card companies may also come after your business with a lawsuit under the Payment Card Industry Data Security Standards (PCI DSS).
Media Liability claims are also possible, where a plaintiff claims copyright infringement. But that’s not all! Although usually insurable under a cybersecurity policy, regulatory penalties, fines, and inquiries are always a looming possibility following a cyberattack. Keep in mind that cybersecurity policies typically have caveats that allow penalties to be applied despite the cyber policy protection.
The FTC and other government regulatory entities that impose these regulatory punishments utilize the NIST (National Institute of Standards and Technology) Cybersecurity Framework. A PAM (Privileged Access Management) cybersecurity solution is an effective way to meet and exceed the control requirements from regulatory bodies such as the FTC.
The key takeaway is that you must thoroughly research your business’s exposure and how cyber insurance policies cover those losses.
Side two: first-party claims
First-party claims are what businesses usually think of when they hear about cyber insurance. This is when a cyberattack or “bad” event occurs on your business, you suffer losses, are seeking guidance, and need reimbursement for said losses.
Cyber insurance coverage can be split into four categories of “bad” events: Data breach or cyber event, ransomware, loss of funds, and miscellaneous but situationally important. These coverage categories can overlap depending on the cyber event.
Learn more: What is Cyber Insurance
Cyber events can impact every part of a business. It is critical for leaders from all departments in a company to meet and identify the cyber risks they potentially face. Only by having a holistic understanding of the entire attack surface can a business get the appropriate cyber insurance. Without determining all potential cyber risks, needed coverage can be missed.
Make sure your concerns are communicated to your insurance broker—you know your business better than the insurance broker!
Prepare to answer the questions cyber insurance providers are sure to ask: Cyber Insurance Readiness Checklist.
What happens after the quote?
After you receive the quote, go over each concern and make sure the cyber insurance policy covers them. Pay attention to limits the cyber insurance policy may have attached to coverage, as it is possible cyber insurance insures a concern only up to a certain limit or not at all. Suppose you cannot get your cyber insurance policy to cover a specific loss to the degree you need. In that case, you should consider using controls such as Privileged Access Management (PAM) to hedge against the issues in question.
Why is renewing cyber insurance difficult?
The cyber insurance renewal process is getting progressively more difficult to achieve for businesses. Cyberattack losses continue to skyrocket, and insurers are requiring increasingly more specific controls before issuing quotes. In many cases, businesses need to implement specific controls before a quote can be bound and a policy issued by the insurer.
Insurers constantly monitor and evaluate industries, business sizes, and business controls to determine if and how they should insure businesses. As a result, an insurer can reject a business’ request to renew an existing cyber insurance policy, even if no cyber event has occurred. Whoever the cyber insurance provider may be, they are all asking the key question, “Whether on-premise, or in the cloud, how hard would it be for a bad actor to access this company’s data?” Keep this question in mind when planning your policy.
Assessing cybersecurity requirements for cyber insurance
While it’s clear that there is an endless number of combinations of ways to increase a business’s cybersecurity, it can be broken down into three categories: people, processes, and technology. Cyber Security is only as good as its weakest link, so it is imperative for businesses to invest in bolstering security in all three categories through education and standardization.
Constantly training people against social engineering threats, phishing, and password safeguards are key to bolstering security. Standardization of security processes tells people what to do and how to do it—the less freedom of choice, the less chance personnel will act in a way that opens the door to bad actors.
Privileged Access Management and cyber insurance
Cyber insurance insurers are always on the lookout for technologies that address important security controls. Since Privileged Access Management implements all the increasingly required security solutions, more insurers are outright requiring a PAM solution to be implemented before a policy can be obtained or renewed.
Conditions are becoming increasingly more dangerous for businesses regarding cyber threats, and the losses incurred are increasing every year. Cybersecurity insurers will continue growing their premiums, reduce coverage, and add exclusions to compensate for the risk they are undertaking. By implementing a robust PAM solution, businesses can not only become eligible for many cybersecurity policies but also outright protect themselves from cyber threats.
Want to learn more about cyber insurance? Download the Conversational Geek: Conversational Cyber Insurance eBook today!
More cyber insurance resources to help you:
Two cyber insurance case studies
Podcast: The Intensification of Cyber Insurance with Ann Irvine and Kevin McGowan
Podcast: Cyber Insurance with the Experts: Michael Phillips and Kevin McGowan

Free Cyber Insurance Readiness Toolkit


