API security and the importance of credentials and access control
APIs have revolutionized the way we develop and deploy software. They’ve also increased the risk of data breaches and cyberattacks. Considering that APIs manage critical functions like server-to-server communications, data processing, and IT system integration, securing APIs is critical to keeping your business operational.
API security depends heavily on implementing strong access controls and safeguarding the credentials that unlock that access. These are also the aspects of API security where many organizations fail. Because APIs run in the background of IT operations, credentials can too easily fall off the radar of a security team, allowing APIs broad access without proper oversight.
In this blog, you’ll learn about the most common API security risks and examples of best practices to mitigate them. You’ll see how attackers find and leverage API credentials to gain access to your IT environment. With this knowledge, you can gain more visibility into your API security posture and start to implement effective API security controls.
Whether you’re a developer who designs APIs, a cloud architect who relies on them, or an infosec pro working to reduce risk, this is information you’ll need to enhance your organization’s API security.
How do APIs work?
The first step to improving API security is understanding exactly how APIs work. APIs define the methods and data formats developers use to request and manipulate information or services from a remote application or service.
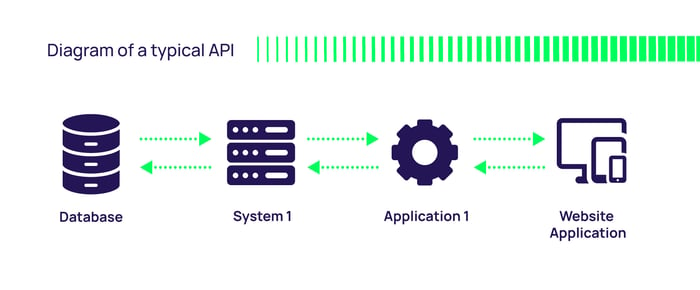
Types of APIs
APIs come in various forms depending on their purpose, which helps you determine the potential security risk and provides guidance on the types of API security techniques and strategies you should employ.
- Web APIs
- Library or Framework APIs
- Operating System APIs
- Database APIs
- Hardware APIs
- Cloud APIs
- Payment APIs
- Mapping and Geolocation APIs
- Messaging APIs
- 1IoT APIs
- Data APIs
- Custom APIs
How credentials impact API security
Whoever has access to an API credential is authorized to make requests to the API so that they can interact with the sensitive data, applications, or web services an API offers.
Two components of API credentials are essential to tightening API security.
- API Key/Token: A unique alphanumeric string acts as a form of identification. It’s supplied by the API provider to the developer or application and serves as proof of identity when making secure API requests.
- Secret: In some cases, an API key or token is paired with a secret, which is a confidential piece of information known only to the API provider and the authorized application. This secret is used to generate cryptographic signatures or perform other API security-related operations.
API security best practices include randomly generating keys and secrets, using different ones for different applications, rotating them regularly, and deleting them when they’re no longer needed. Modern Privileged Access Management (PAM) vaults manage these processes automatically, even at the speed necessary for rapid development cycles and DevOps workflows.
How access controls impact API security
API access controls determine who can access which resources and perform specific actions. There are several levers you can pull that determine the “who, what, and when” of API access control to improve your API security posture.
- Authentication: Your choice of API keys, tokens, or other authentication methods like OAuth 2.0 verify the identity of the user or application making the API requests. For many applications, Single-Sign-On authenticates in the background.
- Authorization: You can determine what actions the authenticated user or application is allowed to perform by defining roles, permissions, and policies.
- Scopes: You can define specific permissions during the authentication process using scopes, allowing fine-grained control over what parts of an API a user or application can access.
- Session Management: Token-based authentication avoids the use of insecure session cookies. You can improve API securing by ensuring tokens have an appropriate expiration date and can be revoked.
Taking a granular approach to access control helps you secure your APIs in line with the Principle of Least Privilege so that people and systems only access the data and functionality they need. PAM solutions allow you to set up risk-based access controls that provide just-in-time, just enough access to improve your API security.
Security considerations for designing APIs
Beyond managing API credentials and privileged access, design best practices will help you improve your API security. When creating your own APIs, double-check that you’ve configured them correctly to eliminate vulnerabilities. If you’re using APIs designed by a third party, confirm that these elements are in place before you integrate them into your IT environment, so you don’t introduce vulnerabilities.
Remember to check for:
- Rate Limiting/Throttling - You can restrict the number of API requests a user or application can make within a specific time frame. This prevents overuse or malicious abuse of the API, which could lead to degraded service quality.
- Encryption - Use encryption to protect data at rest and in transit. Use HTTPS (TLS/SSL) for secure data transmission. Encrypt sensitive data at rest using industry-standard encryption algorithms.
- Error handling - Provide generic error messages to the client, without disclosing sensitive information about the system.
- Input validation - Validate and sanitize all input to prevent SQL injection, XSS, and other injection attacks.
- Gateway configuration – If your APIs are used in the cloud, make sure your API Gateway is properly configured.
- Content Security Policy (CSP) - Implement CSP headers to restrict the sources of content that can be loaded by your API, reducing the risk of XSS attacks.
- Cross-Origin Resource Sharing (CORS) - Configure CORS policies to control which domains can access your API.
- File Uploads - If your API supports file uploads, validate and sanitize uploaded files to prevent security issues like file inclusion attacks and malware uploads.
- Patching - Keep all API components up to date with security patches.
Next, let’s take a look at what can happen if these best practices aren’t followed.
Examples of API security vulnerabilities and attack paths
The most common way attackers gain initial access to your APIs is by leveraging credentials found in code.
Source code is a leaky asset. Developers often secure code in Wikis message boards, and Slack channels. Too often, it ends up in public repositories like GitHub. Unfortunately, much of this source code includes embedded API credentials. On our 401 Access Denied podcast—Discovering and Stealing Secrets with Mackenzie Jackson—GitGuardian shared that they scanned over 1 billion commits in GitHub, and found 10 million secrets, including API keys.
Once an attacker is authenticated with an API credential, they can easily avoid detection because they’re working within expected parameters
Attackers are actively searching these public repositories to find API credentials for nefarious purposes. They use them to gain initial access to APIs and then continue their enumeration to find additional credentials to access more resources in your IT environment. Once an attacker is authenticated with an API credential, they can easily avoid detection because they’re working within expected parameters. That’s one reason API security is such a difficult nut to crack.
With API credentials in hand, an attacker can conduct any number of activities, even if you’ve followed the guidance for secure API design detailed above.
Commonly, they may inject malicious code through SQL injection or NoSQL injection attacks and compromise your systems. For that reason, you should always validate and sanitize user input before processing it within your APIs, and use parameterized queries to prevent injection attacks.
APIs can become targets of DDoS attacks, which can overwhelm your infrastructure and lead to service disruptions. These attacks can be especially damaging when APIs are hosted in the cloud. To improve your API security, you should always employ DDoS mitigation solutions and traffic monitoring to detect and mitigate DDoS attacks promptly. Cloud-based DDoS protection services are key if your APIs are hosted in the cloud.
Manage DevOps secrets safely
Hacking scenarios to test and improve your API security skills
A great way to improve your understanding of API security is to reverse engineer the attack path a hacker would take in real-life scenarios. You can use the Hackthebox platform to play with APIs that are set up for this purpose.
Hacking scenario 1: Exploiting weak credentials

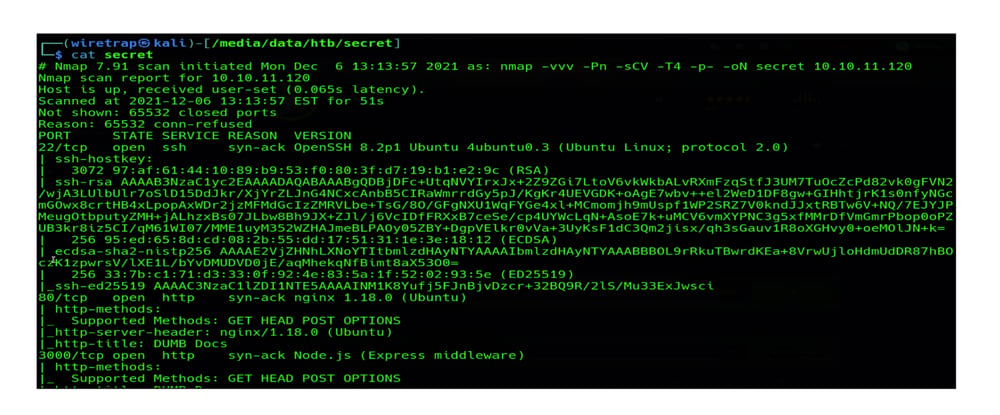
Hackthebox’s “Secret” is a retired Linux machine of easy difficulty. It uses a custom API with weak authentication. To mirror a hacker’s attack path, you can perform a typical reconnaissance of the machine, which reveals three open ports: Port 22 – SSH, Port 80 – NGINX, and Port 3000 – Node.js.
Exploring the website reveals details on API-based authentication, installations, and additional details. It also makes the source code available to download.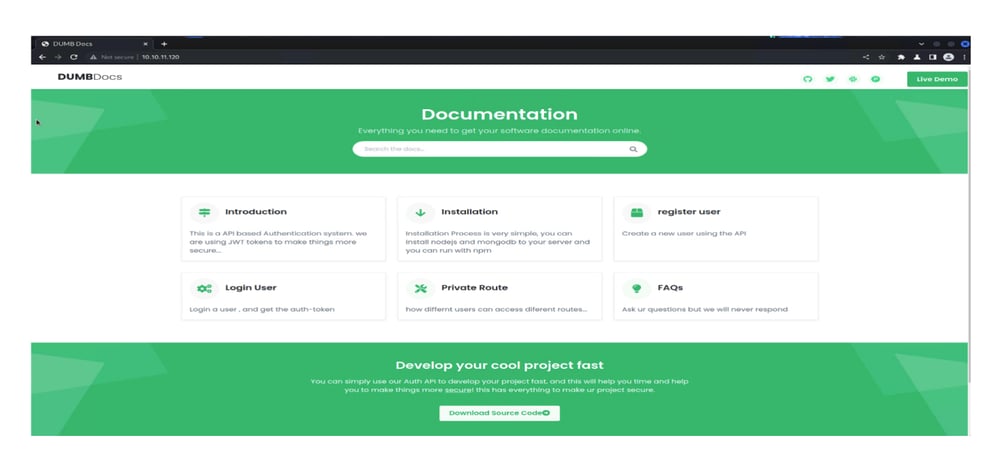 After downloading the source code, it reveals a .git repository that contains several commits.
After downloading the source code, it reveals a .git repository that contains several commits.
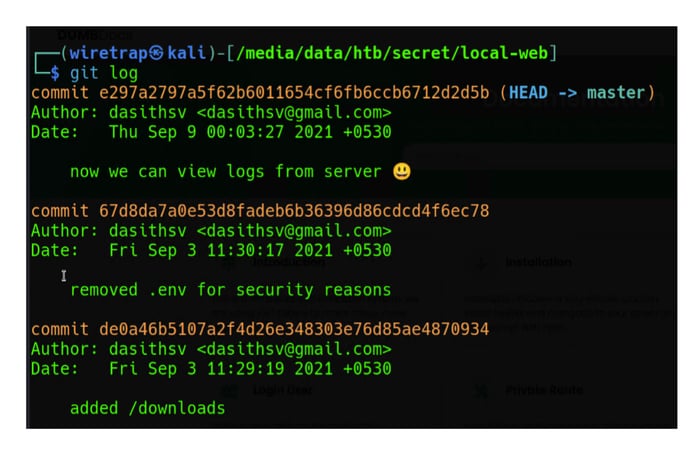
Exploring the .git commits reveals details of a change to the code that removes a hardcoded token and replaces it with the generic “Secret.”
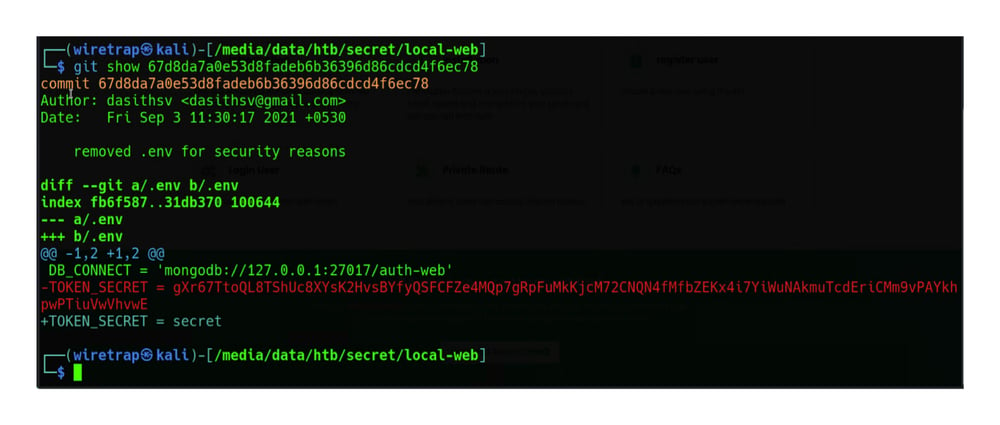
Once you have knowledge of the token, you can forge your own tokens and find ways to gain access to the site and system.
 Manage credentials for applications, databases, CI/CD tools, and services with Delinea DevOps Secrets Vault
Manage credentials for applications, databases, CI/CD tools, and services with Delinea DevOps Secrets Vault
Hacking scenario 2: Exploiting misconfiguration

In this scenario, a hacker takes advantage of an API endpoint that doesn’t adequately protect data and inadvertently exposes information through an error message. “Monteverde” is a Windows machine Hackthebox has made available that demonstrates how exposed configuration files with hardcoded credentials can lead to endpoint compromise.
Here's how it works.
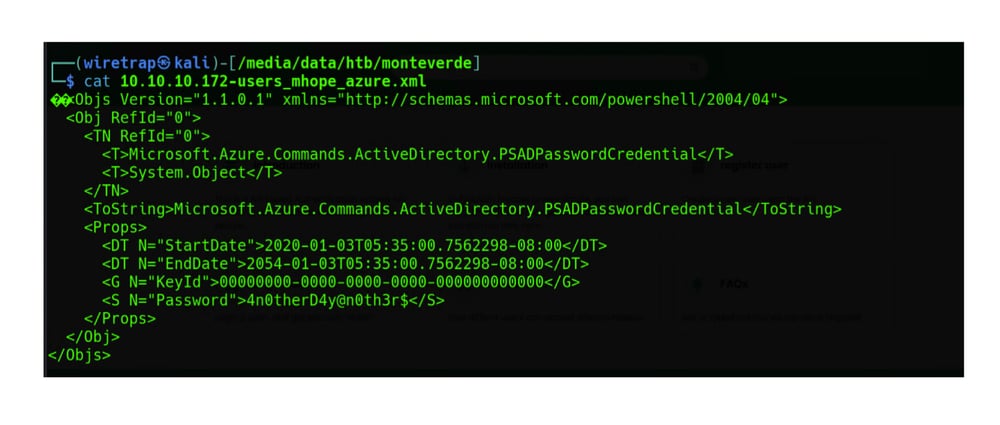
Hackthebox’s “Monteverde" is a Windows machine of medium difficulty and features Azure AD Connect.
After gaining access via a weak credential found through reconnaissance of the machine, you’ll see configuration files that expose the domain administrator’s credentials. In this case, sensitive information wasn’t encrypted or masked. It shows up in the error message.
API security resources to build your skills
API security is becoming increasingly challenging as cybercriminals are constantly evolving their strategies. The cyber community has a number of resources to help you keep up with the latest techniques and implement best practices for API security. Here are some excellent ones you should check out:
The OWASP API Security Project
As with other OWASP projects, the API Security Project benefits from the collaboration of a diverse community of experts. This collaborative approach ensures that the guidance and resources provided are relevant and up to date. The Project does a number of things:
- Documents common API security threats and risks.
- Provides guidance for designing, implementing, and securing APIs
- Offers tools and resources to enhance API security, such as libraries, middleware, and frameworks to implement security controls effectively.
- Helps organizations improve the security of APIs through security testing, including vulnerability scanning and penetration testing.
This is a great resource for free, hands-on courses dedicated to API security.
"Hacking APIs" by Corey J. Ball will teach you how to test web APIs for security vulnerabilities. You’ll learn how the common API types—REST, SOAP, and GraphQL—work in the wild and how to set up an API security testing lab to perform common attacks, like those targeting an API’s authentication mechanisms and injection vulnerabilities commonly found in web applications.
You’ve got this!
Implementing the recommendations in this blog will help you eliminate vulnerabilities in your APIs and reduce the risk of data breaches and cyberattacks. Document your API security policies so that anyone designing, implementing, or managing access to APIs has a checklist to follow.
Also, make sure you monitor the use of APIs and conduct regular penetration testing to confirm that security controls are working as you expect. Then, you’ll be able to demonstrate to any auditor, regulator, or cyber insurance provider that you’re doing all you can to ensure API security.