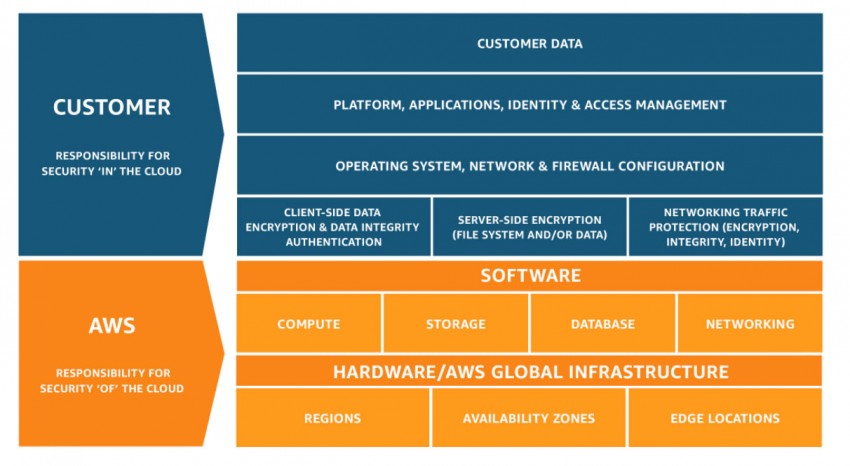
Amazon Web Services (AWS) gives IT and development teams tools to move fast and change direction on a dime. Privileged accounts for AWS resources are created quickly and maybe abandoned just as quickly. With such a fluid process, it’s difficult for security teams to stay on top of how many privileged accounts have access to AWS, make sure they’re set up properly, and remove them when they’re no longer needed.
PAM oversight is especially important to secure systems like AWS, which are easily misconfigured, inviting attacks.
Essential PAM controls for AWS
PAM solutions are designed to enforce consistent PAM best practices every time a new AWS account is set up, whether that’s by the security team, the infrastructure team, or a single developer building an application.
When you set up compute resources with AWS there are several actions you can take to reduce risk:
• Secure AWS privileged credentials in a PAM vault
• Automate high-speed secret creation, archiving, retrieval and rotation
• Limit access to the AWS control panel
• Confirm MFA is required for root access to AWS
• Set up session monitoring and recording for root account activity
• Add in workflow rules for approval or dual control
Additionally, to match the fluid nature of these accounts, continuous AWS account discovery is an essential cloud security control PAM teams need in their arsenal. It gives you the visibility to check that best practices are being followed.
What about native IAM/PAM capabilities offered by AWS?
AWS does offer capabilities to manage identities and privileges. For some organizations, these controls are enough to get up and running. Certainly, they are better than no PAM at all. These controls are stretched when addressing the more advanced requirements of PAM, especially in hybrid or multi-cloud environments.
As a PAM leader, your goal is to empower your entire company to follow consistent PAM policies, whether they’re using AWS, Azure, SaaS, or on-premise solutions. When you set up session management rules or run reports for compliance, you’ll want to see all privileged account usage in a single, consolidated view. It’s more efficient to manage AWS credentials from your central PAM solution, rather than implement a special purpose tool that only works on one IaaS platform.