5 Myths about privileged access security for AWS
I may be stating the obvious, but the cloud is not a fad. Organizations continue to migrate workloads to AWS, Microsoft Azure, Google Cloud, and similar platforms. As Gartner told us way back in 2016, it’s a business imperative: “Organizations embracing dynamic, cloud-based operating models position themselves for cost optimization and increased competitiveness.”
While larger organizations operate in a hybrid model with IT infrastructure, apps, and data both on-premise and the cloud, the momentum clearly shifts towards the cloud. Experts used to recommend keeping sensitive assets on-premise where IT could better protect them. However, according to the Flexera 2021 State of the Cloud Report, 92% of enterprises claim to have a multi-cloud strategy, and 80% own a hybrid cloud strategy, proving that resistance has evaporated.
Security teams must adapt. It’s critical to understand what existing security processes, controls, and products you can leverage in the cloud, and which ones you can’t or that may require new approaches.
In the rest of this blog, we’ll highlight some of the myths we hear regarding privileged access security in AWS and ideas for tackling related concerns.
AWS Myths: Separating Fact from Fiction
- AWS provides all the security your organization needs
Let’s say you stand up EC2 instances in new VPCs to run your apps. You may have dozens for different projects. Will AWS govern and protect access to the instances and the sensitive apps/data they contain?
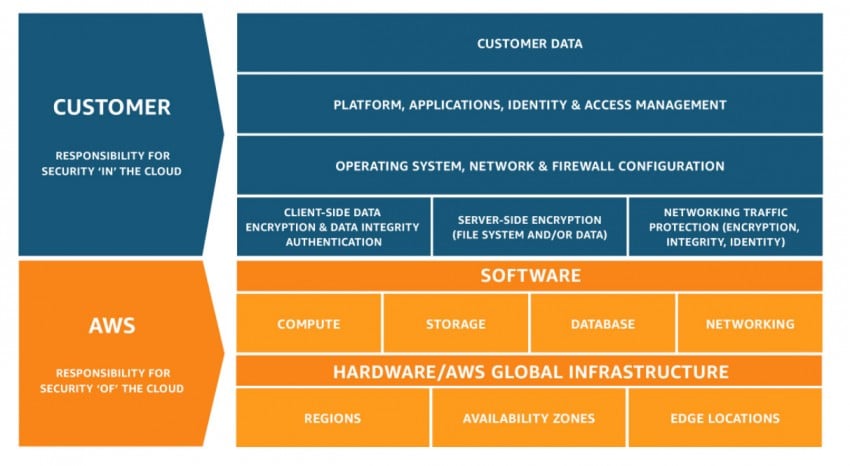
Security and compliance are a shared responsibility. AWS’s responsibility is the security “of the cloud,” from the host operating system down through the virtualization layer to the physical systems and facilities. You own security “in the cloud” - the guest operating system, applications, services, and data that reside on top.
Regarding Privileged Access Management (PAM), you are responsible for the policies and controls that ensure the right users can log in to specific EC2 instances and containers, when and for how long, and what applications and commands they can run.
- Cloud adoption requires a new PAM model
Can you extend an incumbent, on-premise PAM solution to secure your cloud workloads? AWS’ published security best practices recommend that “conventional security and compliance concepts still apply in the cloud.”
Delinea agrees that your incumbent PAM policies and procedures are relevant, as are PAM-related technologies such as Active Directory, LDAP, MFA, and SIEM tools such as Splunk. However, your PAM solution may not be 100 percent suitable. Many PAM vendors designed their solutions when systems, users, and PAM software were on the same network.
You must assess its applicability for a modern distributed IT model. Can you extend its reach to the cloud without losing functionality? Can you replicate your PAM stack in the cloud? Either option will add complexity, operational overhead, time to productivity, and risk.
Another option is to modernize; replace it with a PAM solution designed to accommodate a hybrid cloud model.
- Adopting hybrid cloud means building a new identity infrastructure
Your administrators must be able to access IT infrastructure wherever it lives using their enterprise identities. On-premise, your systems can easily validate users against Active Directory or LDAP. Inside a private AWS VPC, virtual instances have no such line of sight.
You could use local accounts, extend your network with a site-to-site VPN, or replicate directory infrastructure in each VPC. These options are not ideal, increasing your attack surface, costs, complexity, administrative overhead, and risk. A modern PAM solution can broker identities from any enterprise directory without such issues and without breaking the private nature of your VPCs.
Don’t forget access to AWS services via the AWS Management Console or programmatically via AWS APIs and CLIs. You should avoid AWS’s IAM service to create local user accounts and AWS Access Keys, adding another silo of identities. Let your PAM solution federate your enterprise identity via SAML.
- Establishing equivalent security and compliance for the cloud will delay projects
Can IT and security execute quickly enough to keep pace with aggressive cloud transformation agendas? This is achievable by building off AWS’s security best practices and applying your on-premise privileged access security model. However, nuances of a hybrid cloud model may stretch a legacy PAM solution too far, causing delays.
With the proper guidance and proven best practices, this migration can be more efficient and secure. With a modern PAM, you quickly secure new EC2 instances by deploying PAM clients and enrolling them in the SaaS policy server. You don’t have to sacrifice security, compliance, or time when using a unified security model as you migrate your data and applications to AWS.
- Adopting cloud will give us agility, but at the expense of security
The cloud can make you more agile, but at what cost? Does adopting the cloud mean your company is at a higher risk of a data breach?
The cloud is, by nature, elastic. It can automatically adjust to avoid resource overprovisioning and under-provisioning. If you must deploy and configure PAM policies and controls manually, you can’t keep up, and security will suffer.
You must be able to discover EC2 instances continuously and then fully automate the PAM processes: vaulting local privileged accounts, deploying and enrolling PAM clients, and configuring appropriate roles and rights just-in-time so that your IT, Security, and DevOps teams can access them securely.
Applying what already works on-premise to your hybrid cloud makes retaining control over infrastructure and applications on-premise, in a private cloud, and a public cloud feasible. With fewer identities and a least privilege model, the potential for a data breach is minimized. Indeed, security controls for the cloud are not much different than those you are already using on-premise.
In summary, there are many security myths concerning AWS. Following good best practices such as least privilege, Zero Trust, and zero standing privileges as you do on-premise is a robust foundation. However, a modern approach to PAM in line with modern hybrid cloud use-cases is equally essential.
Learn more about Delinea’s modern PAM solutions.