Evolving DevSecOps with Delinea Delegated Machine Credentials
Delinea is excited to have been awarded Patent #11,706,209 by the US Patent and Trademark Office for Delegated Machine Credentials. This feature is a part of our Delinea Cloud Suite solution. This patent is Delinea's 18th and the first one awarded since Centrify and Thycotic merged.
Why did Delinea develop this?
One critical task that falls on IT's shoulders is ensuring business workloads—applications and services—can authenticate to other applications and services. Failing can significantly impact the business, including disruption of business operations, loss of revenue, non-compliance, reputation damage, increased support costs, and security risks.
How has this been solved traditionally?
There are several approaches to managing credentials for apps and services that need to authenticate with each other, the most popular one being Application-to-Application Password Management (AAPM.)
With traditional AAPM, privileged account passwords are protected and managed in a vault instead of being embedded in scripts and application code. As needed, the workload obtains a vaulted credential via SDK tools that interact with the vault to check out and retrieve the password at run-time.
What are the main pros and cons of AAPM?
A threat actor can harvest hard-coded, plaintext, or improperly stored credentials to jeopardize security for the workload or the entire system by facilitating lateral movement. By eliminating passwords from code, you eliminate that risk.
The main con is operational overhead, all the work involved in enabling workload-to-vault interaction. However, this overhead is not just a few new SDK calls for the developers. There are additional (typically manual) things your Ops or Security team must do to enable this:
For each workload, the general process is as follows:
- Create a service account and an OAuth client app in the vault on a per-workload basis.
- Delegate the necessary permissions for each service account and scope access to only those vault APIs needed for the workload.
- Embed an OAuth client and Secret in the workload code to authenticate to the vault and retrieve a scoped token.
- At run time, authenticate to the vault with the Secret, then call the required APIs using the retrieved token to access the needed vaulted resource(s.)
For at least two decades, this AAPM model hasn't changed. While the cybersecurity pros have outweighed the operational cons for many organizations, that balance has shifted for organizations transforming their business and adopting modern, cloud-based services.
Your applications and services may number in the millions, which should illuminate the scale of this service account management challenge and the enormity of the identity attack surface. Of course, sharing accounts can reduce the service account sprawl, but the negatives include lost accountability, limited ability to monitor and audit usage, and increased vulnerability to cyber criminals. The overhead of managing things like account and password creation, deletion, and rotation is enormous.
How does Delegated Machine Credentials change the game?
Delegated Machine Credentials provide benefits for your developers and operations team.
Invented by a Delinea Distinguished Engineer, Nate Yocom, Delegated Machine Credentials modernize AAPM, evolving DevSecOps to incorporate Privileged Access Management (PAM) into the DevOps pipeline.
Delegated Machine Credentials separate the management of identities and access rights from the workload authentication logic, reducing pain and friction at the intersection of workloads and service identity.
The solution works by installing a Delinea Cloud Suite client on a VM, which is easily done through a user data script or orchestration tooling. The only requirement is a registration code from Cloud Suite. Instead of authenticating to Cloud Suite directly, workloads request a short-lived OAuth bearer token from the Delinea client, piggybacking on its trust relationship. Delinea provides developers with standard code snippets to help with this.
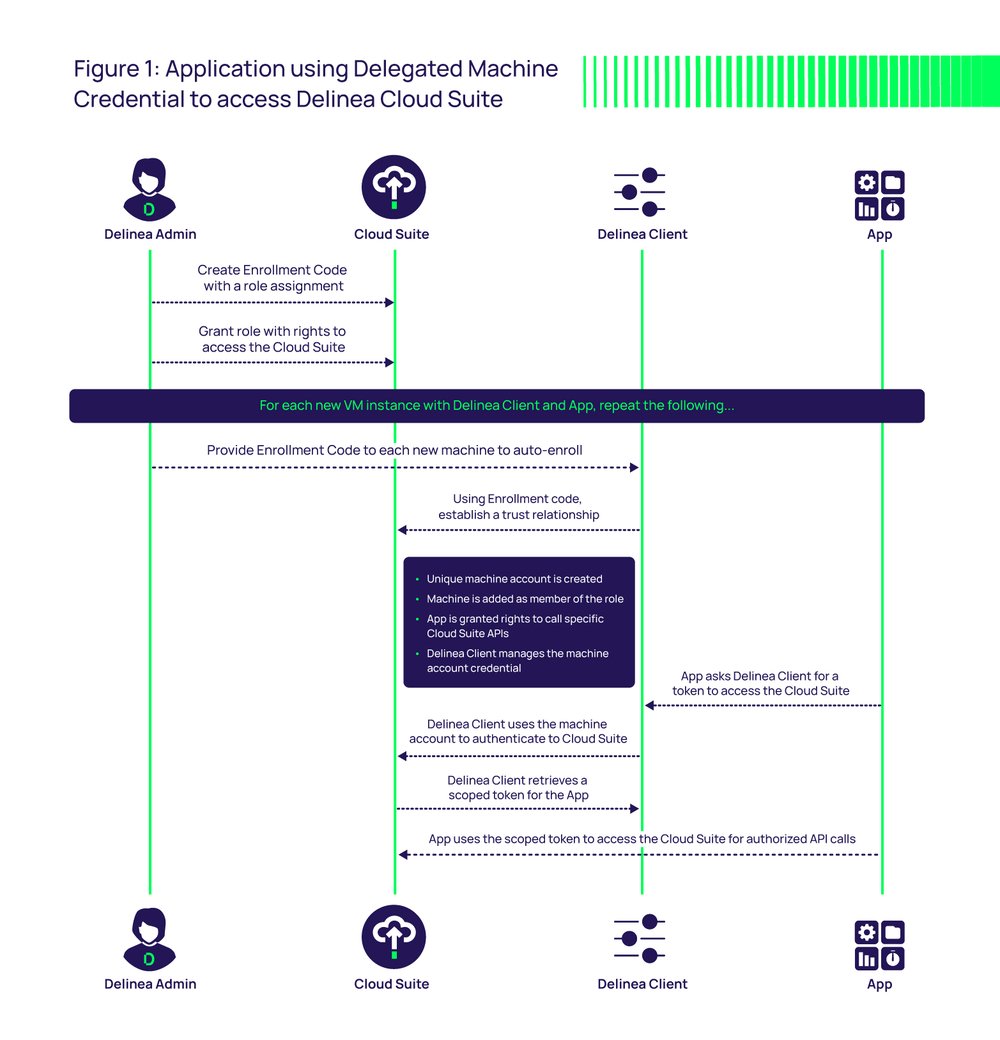 The Delinea client authenticates to Cloud Suite on behalf of the workload and (if permissions are valid) receives a scoped OAuth2 bearer token that it hands back to the workload. This token authorizes the workload to make subsequent API requests without having to authenticate using a dedicated service account. Reducing the number of service accounts from one per workload to one per machine and automatically managing them reduces your attack surface and operational overhead.
The Delinea client authenticates to Cloud Suite on behalf of the workload and (if permissions are valid) receives a scoped OAuth2 bearer token that it hands back to the workload. This token authorizes the workload to make subsequent API requests without having to authenticate using a dedicated service account. Reducing the number of service accounts from one per workload to one per machine and automatically managing them reduces your attack surface and operational overhead.
Your operations team benefits as well. The registration code provided to the VM enables the operations team to centrally define and manage all permissions and scopes for named workloads on that VM. The operations team can adjust permissions, control API scope, and configure password policies to ensure vaulted workload passwords are unique, complex, and rotated on a schedule. Thus, when passwords change, there's no business impact. Workloads continue to function, and developers are relieved of having to update, test, and publish new code.
Many organizations undergoing cloud transformation are modernizing their workloads to take advantage of tokens for AAPM. The same workflow described above supports this model with Delinea Cloud Suite able to mint short-lived OAuth tokens for workloads instead of passwords.
What are some use cases and examples of delegated machine credentials?
There are several examples of how you can use this:
Delinea CCLI for command line access
Here is a REST API tool that gives you a command line interface to the Delinea REST API. The tool supports searching and listing Delinea API endpoints, JSON schemas of the Delinea API endpoints, and handling authentication via OAuth or user ID and password.
Delinea Terraform Provider for Delinea Cloud Suite
A Terraform plugin that allows other Terraform scripts to retrieve a vaulted password or Secret. It also enables complete configuration management of Delinea Cloud Suite.
LRPC for Delinea Cloud Suite token request
The Delinea Cloud Suite client supports a native Lightweight Remote Procedure Call (LRPC2) service. With this, applications can call Delinea Cloud Suite to request a scoped token.
An example of this is in the lrpc2.cs GitHub code for the Delinea CCLI tool in the first example above.
Try it out
Get a trial of Delinea Cloud Suite today, and be sure to download the Delinea CCLI utility to try out Delegated Machine Credentials for your automation scripts.
Watch our webinar: Service Account 101: How to Start Managing Your Service Accounts
Related Reading: Securing DevOps with Delinea delegated machine credentials