Top 8 cloud security questions to ask any PAM vendor
You’d think strong security would be table stakes for any cloud PAM provider, right? The truth is there are many factors that contribute to the security of a PAM solution, and not every provider prioritizes them.
Here are eight security-focused questions you should ask your PAM vendor. By asking these questions, you’ll be able to assess the security of any cloud PAM solution you’re considering and more quickly make a confident decision.
1. With your PAM solution, how do my developers get access to customer data in SaaS applications?
Most of the hacks that are in the news are related to internal controls within the company that is running the SaaS service. Your PAM solution should offer numerous formal controls to provide access. For example, users should go through jump boxes. Their requests should be confirmed by multiple approvers. Authentication should offer multiple MFA options. When access is granted, it should only be on a temporary basis; access should expire at a specific time.
2. Do you have built-in redundancy?
Redundancy is closely related to security. Without built-in redundancy, you have a single point of failure, a window that gives attackers an opening to find a way inside. Beyond improved security, there are many benefits to built-in redundancy for your PAM solution, including cost savings and business continuity. Learn about how Delinea's cloud-native architecture improves resiliency.
3. How well can you scale as demand increases?
Scale is essential for security. If you can’t keep pace with business needs and development timelines—if users need to wait to get access because the system is overloaded at peak times—they’ll find ways to skirt security controls to keep the job done, which increases your risk. The benefits of an auto-scaling PAM solution go beyond improved security. Auto-scaling saves you money and reduces time and effort managing your PAM solution. Read about how we’ve designed Delinea's Cloud PAM architecture for scalability and lower total cost of ownership.
4. How does your PAM solution help me discover new cloud privileges?
Eliminating unknown, unmanaged accounts is a PAM best practice. But your cloud security posture is a moving target. Every time a new cloud instance is created or someone is provided privileged access to your cloud platforms, your attack surface grows, and your risk increases. Ask your PAM solution vendor how they’ll help you stay up to date. Can they automate continuous discovery? Just for one cloud platform, or across multiple clouds? The sooner you discover rogue accounts or unprotected access, the sooner you can make sure all accounts are governed according to your PAM policies.
5. How is my sensitive data isolated from other companies?
A cloud PAM platform hosted on Azure, for example, can be architected with shared infrastructure for cost and efficiency savings. If your passwords, secrets, and keys are sitting in a vault on a shared tenant, your PAM vendor should verify tenant data isolation. Only the people you choose should be given access. There should be no cross-over between your resources and any other customer of that vendor.
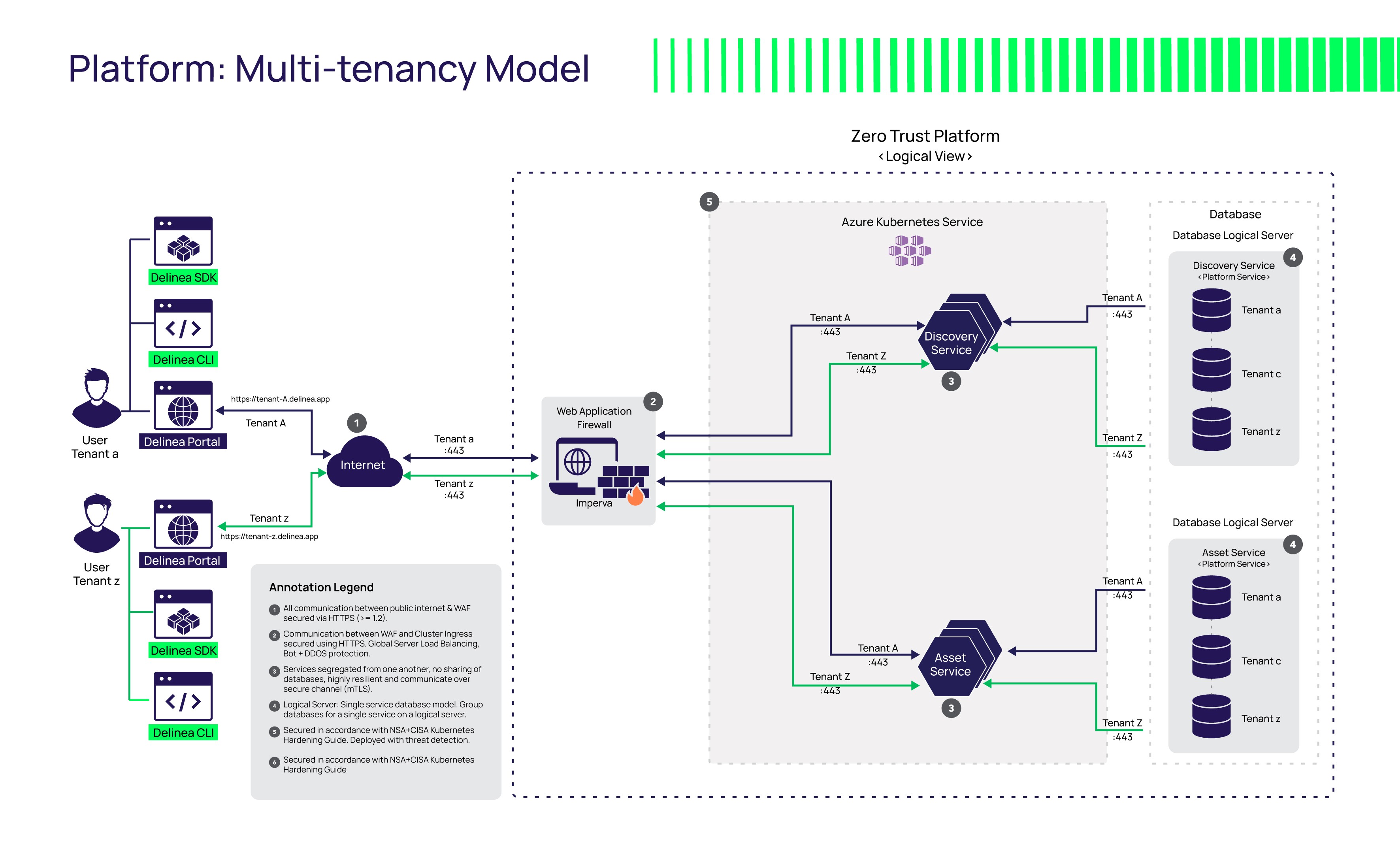
6. How strong is your encryption?
AES 256-bit encryption is the strongest encryption available for PAM software and provides unsurpassed security. In addition to at-rest encryption of secrets, security can also be used with SQL Server Transparent Data Encryption (TDE) for further data protection. SSL/TLS can be enforced on all connections to ensure end-to-end encryption. Visit the Delinea Trust Center to learn about how Delinea’s solutions are built with security as the foundation.
7. How do you validate your software security?
PAM vendors should frequently scan their source code with multiple types of scanning tools, looking for security vulnerabilities and embedded secrets, and offer proof of penetration testing. Pen tests should happen at least once each year or upon every major software update. They should be conducted by external assessors, using both automated and manual methods to replicate the mindset and strategies of a hacker.
8. Can I do a POC to try the user interface before I buy?
Security that isn’t usable will take many months to implement and struggle to gain adoption. Push your PAM vendor to let you experience the product so you can get a realistic feel for how it works and measure ease of use. You may find that you’ll need to engage their pro services team or hire multiple people to manage your PAM solution because it’s so hard to use, driving up your overall cost of ownership. Or, you may find that it can be managed as part of one person’s job, freeing up hours and dollars for other value-added projects.
Speed your PAM evaluation
Include these questions in any RFP you develop for a cloud PAM solution and ask them of any vendor during your product demonstration and Proof of Concept.
Or start your 30-day trial of Secret Server on the Delinea Platform today.
IT security should be easy. We'll show you how