Protect against identity-based attacks with identity threat detection and response
Securing your identity threat surface has never been more challenging. It’s also never been more critical.
Attackers know the path of least resistance and consequently, the biggest payoff is to use compromised credentials to gain privileged access to their targets’ most sensitive assets. According to the Verizon Data Breach Investigation Report for 2022 (DBIR), 48% of breaches involved the illegitimate use of credentials.
As you transition to the cloud, your identity perimeter keeps growing. More identities across more cloud environments will challenge your security team to answer the following questions:
- What are our identities doing with their access privileges?
- Do we have over-privileged or stale accounts that harm their identity risk posture?
- Are we at risk of privilege escalation?
- Are there impersonation attacks on our Identity Provider (IdP)?
- Are new admins being illicitly created?
- Can we detect suspicious identity activity?
- And can we respond effectively if we detect a threat?
Adding to these challenges, attackers aren’t only looking to compromise identities. Adversaries are also working to undermine the very systems you depend on to manage identities, increasing the risk security teams contend with.
To face these challenges, forward-thinking security teams are embracing a new approach that treats identity like all the other threat surfaces, by securing it with the same granularity and consistency as they would their endpoints, networks, and cloud platforms.
Identity Threat Detection and Response closes security gaps
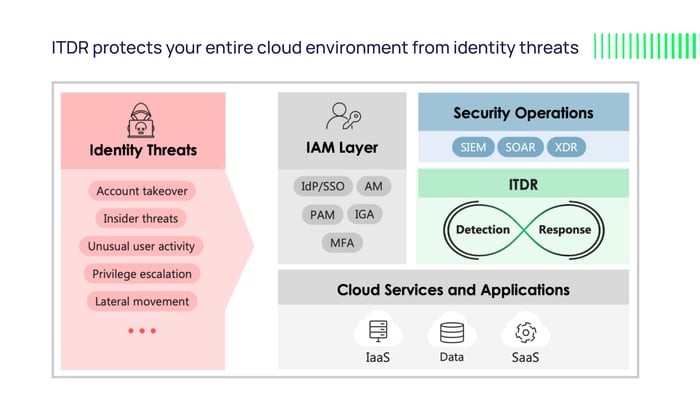
Identity Threat Detection and Response (ITDR) is an emerging cybersecurity discipline that closes gaps exposed by Identity and Access Management (IAM) systems.
“Organizations have spent considerable effort improving IAM capabilities, but much of it has been focused on technology to improve user authentication, which actually increases the attack surface for a foundational part of the cybersecurity infrastructure,” Gartner has reported. “ITDR tools can help protect identity systems, detect when they are compromised and enable efficient remediation.”
Existing IAM tools are created as management tools rather than security tools. They aren’t proactively monitoring for breaches of policy or configuration. While IAM tools can be used to audit changes after the fact, they can’t detect breaches in near real-time.
ITDR adds a necessary layer of security to reduce risk, identify threats, aid in response, and validate that IAM systems aren’t compromised.
Security response orchestration
In the event of a security incident or policy violation, ITDR will generate alerts and trigger actions in another system to remediate the problem. For example, when ITDR detects that an identity is being abused, it can trigger removal of privilege from that identity.
Mitigate access risks with just-enough privileges
Protecting against identity-based attacks requires mitigating risks that allow for account takeovers and privilege escalation across your IaaS, SaaS, and IAM environments. Detecting stale accounts and privileges, over-privileges, and other hidden risks is the first step to mitigation. Afterwards, you can remove those risks to limit a malicious actor’s ability to exploit access and cause damage.
Detect and respond to active identity and access threats
Reducing risks by removing stale accounts, privilege escalation paths, over-privileges, and misconfigurations in IAM is an important step for achieving a state of Just-Enough Access. ITDR identifies these risks, making your organization a harder nut for attackers to crack.
Despite your best efforts, threat actors will still target your identities in an attempt to exploit their access and reach your valuable data. It’s up to you to identify their malicious activities and respond effectively.
This is where ITDR’s continuous monitoring of your IaaS, SaaS, and IAM environments enables you to detect:
- Impersonation attacks originating in the identity infrastructure
- Suspicious / anomalous login activities
- Potentially malicious changes to identities and access privileges
- Privilege escalations as they happen
- Known and unknown attacker Tactic, Techniques, and Procedures (TTPs) based on observed activities affecting identities, access privileges, and sensitive (virtual) assets
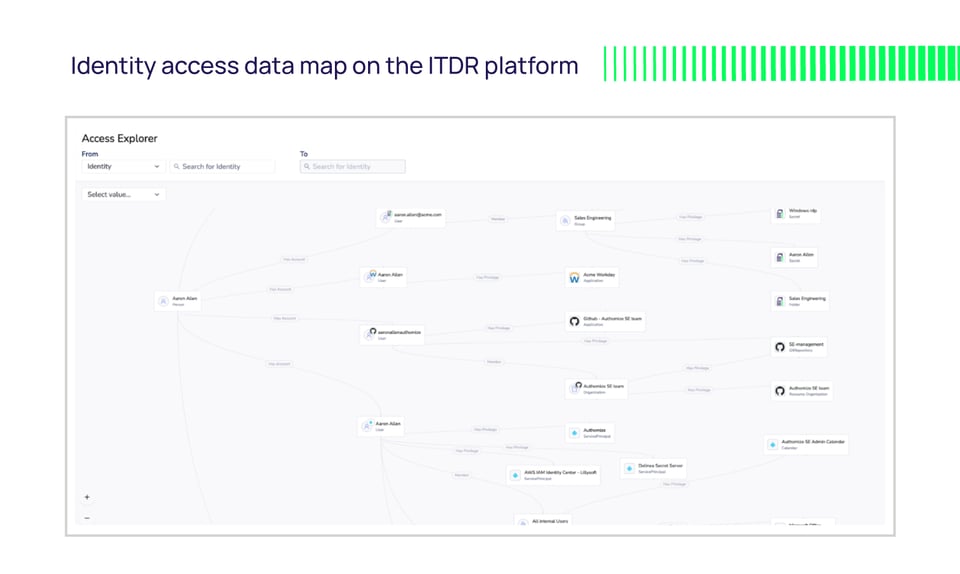
Once potentially malicious activity is detected and notifications are sent, security teams can use the identity and access data on the ITDR platform to investigate incidents quickly and effectively, automating many investigative processes to save time and cost. Because all identities, assets, access privileges, and activities are mapped out and logged in the ITDR solution, investigators have the required context at their fingertips to assess and act.
Security teams can then operationalize this contextual identity data as part of a holistic security operations response workflow, sending alerts to their SIEMs, SOARs, XDRs, and other centralized security orchestration systems to prioritize and resolve an incident. Teams have this data available for investigating not only identity-based alerts, but also for all security incidents that arise, adding valuable insights that make it easier to understand what systems and data an attacker may have accessed.
 Authomize extends Delinea’s security offering with ITDR
Authomize extends Delinea’s security offering with ITDR
As the industry’s first ITDR platform, Authomize gives Delinea customers the ability to:
- Harden your identity security posture with just-enough access everywhere
- Detect active threats across clouds (IaaS and SaaS) and IAM infrastructure
- Respond effectively and in line with security operations policies and procedures
- Accelerate investigation and prioritize actions with context
Native integration with Delinea Secret Server, enables organizations to gain total visibility and control over all their identities’ access privileges from their vault across IaaS and SaaS applications.
Hardening your posture is just the first step. Working together, Authomize enables Delinea customers to detect and respond to active threats to continuously maintain cloud security.
Take the first step: Understand your identity security risk
Get a free report on the state of your identity security risk. The tool will discover and report on risks in your identity infrastructure (e.g. stale or unused accounts, shadow administrators, overprivileged identity accounts without MFA protection, etc.). No installation is required, and your results are completely private and secure.
Visit Authomize to learn more about our ITDR platform and get your free assessment report here.