New research from Delinea reveals cloud automation is critical to future-proofing cybersecurity
The cybersecurity landscape is rapidly changing as companies transition from the pandemic and assess their changing security needs.
As a new Delinea report explains, businesses need to shift their focus from merely surviving to embracing new security strategies that enable them to thrive in today’s unpredictable world. Security leaders need to take an honest look at the security challenges they’re up against—and future-proof their solutions to protect against today’s sophisticated and evolving threats.
With all this in mind, let’s take a closer look at some of the key findings from the report and explore the major security challenges businesses are facing as the pandemic enters its third year.
What are the top security challenges for businesses?
Security challenges are becoming increasingly dangerous and complex, putting more pressure on companies to tighten their postures. The new report outlines three security challenges that companies can expect moving forward.
1. Ransomware
Ransomware continues to stymie businesses and pose a major threat to operations. It’s clear ransomware actors are becoming stronger and more sophisticated. Unfortunately, as a result, businesses continue to pay ransoms and incentivize criminals to continue such attacks.
That said, it's worth reiterating that the FBI does not recommend paying a ransom in response to an attack. As the FBI explains, paying a ransom doesn’t guarantee that cybercriminals will return your data. At the same time, it encourages perpetrators to keep targeting victims and incentivizing others to participate in cybercrime.
2. Access controls for remote workersRemote and hybrid work is here to stay, with most companies now operating in highly distributed environments. Despite this, many companies still lack secure access controls for cloud applications—which is a significant cause for concern.
Without strong access controls, companies can easily lose track of sensitive data and workflows. This can open the door for unauthorized human and non-human identities to access and exploit private assets.
3. Changing IT environments
Widespread digital transformation and cloud migration are taking place as companies embrace new technologies and transition from on-prem systems to hybrid and multi-cloud environments.
On one hand, digital transformation and the cloud can boost security and productivity. On the other, they can introduce new security concerns—like misconfigurations and weak data governance.
Updating your IT environment and embracing new cloud-based technologies also requires modernizing your security posture. Companies that continue to use outdated and inefficient security policies in the cloud risk losing control over their computing environments.
Key takeaway: Security overconfidence is a top threat
Based on our research, companies are very confident in their ability to handle an incoming cyberattack. Our research found that 71% believe they can recover quickly from an attack, and over 80% say that their current access controls meet the needs of their business.
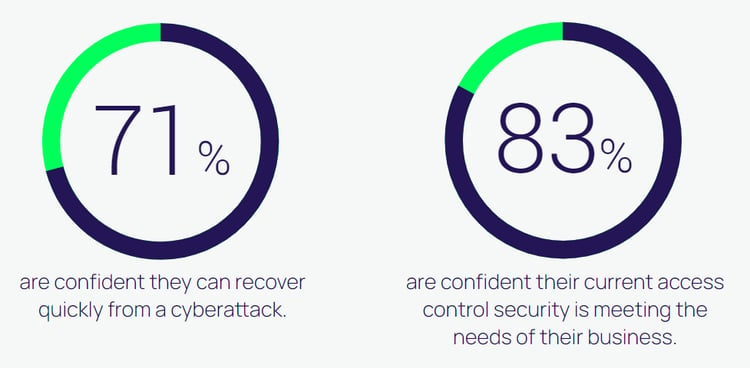
This is a concerning discovery—especially when considering that overconfidence can leave organizations highly vulnerable to attacks. As recent events indicate, now is not the time to have a false sense of security.
Access the full report for more key takeaways and recommendations
To adapt to a more complex, rapidly-changing world, companies need to future-proof their security technologies and modernize their strategies. This is critical for combatting evolving threats and protecting unauthorized users from accessing sensitive information.
For more security tips and insights on how you can fortify your digital infrastructure, download your free copy of Delinea’s report: Cloud Automation is the Key to Future-Proofing Cybersecurity

FREE EBOOK
Increased cloud adoption poses greater security risks to your IT and business users


