Closing the security doughnut: Why CISOs need to prioritize business application security
As systems and users become increasingly interconnected, it’s more important than ever to have a strong security posture to mitigate external and internal threats to systems and data.
However, the security of critical business applications, where sensitive data and financials reside, is often overlooked in the broader strategy for securing an organization’s assets.
Think about enterprise security as a doughnut. The round exterior of the doughnut is where most security measures are put in place to stop external threats. But often, the hole in the middle of the doughnut, where the business applications reside, lacks sufficient security.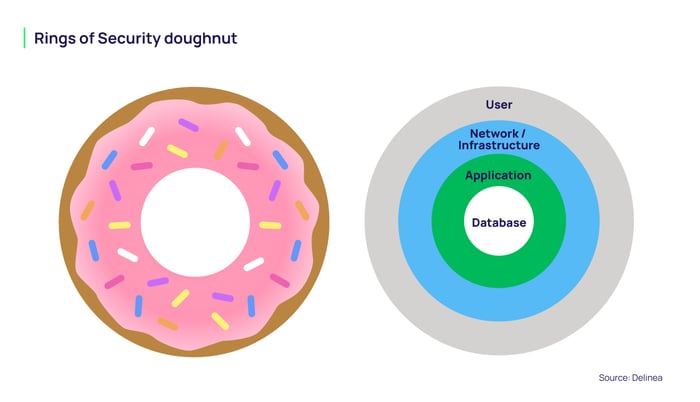
The evolution of the business application landscape
Why is this the case? Let’s take a look at the evolution of the business application landscape. If we go back 40 years, billing systems and accounting software ran on mainframes. Then, in the 1990s, the Enterprise Resource Planning (ERP) system emerged, combining finance, human resources, supply chain management, and other business functions into a single platform. In the 2000s, cloud-based ERP systems started gaining traction.
Today, we see most companies running cloud-based ERP applications as well as best-of-breed applications for other functions, such as procurement, Human Capital Management (HCM), and Customer Relationship Management (CRM). In fact, many organizations have 10 or more business applications, often because of the integration of new technology through mergers and acquisitions.
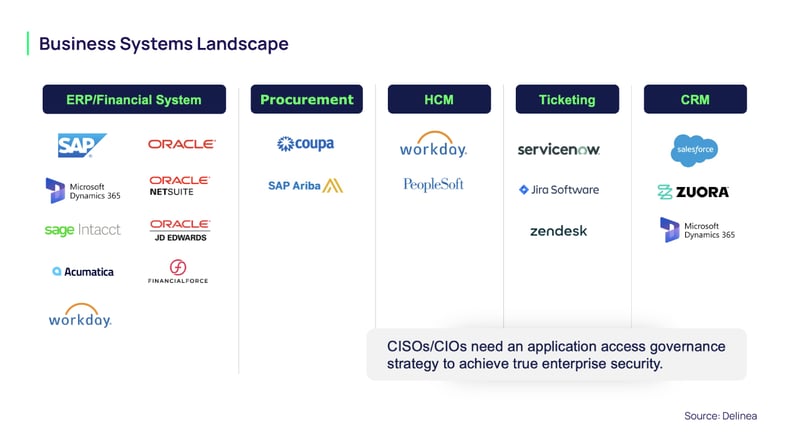 The security doughnut challenge appears with silos of ownership. The accounting or ERP application is owned by the CFO. The HCM application is owned by the Chief People Officer. The CRM application is owned by the head of Sales or the Chief Revenue Officer. Do all those business owners know the expectations for securing their applications? Do they know which security framework the company is following to ensure the right policies and procedures are in place?
The security doughnut challenge appears with silos of ownership. The accounting or ERP application is owned by the CFO. The HCM application is owned by the Chief People Officer. The CRM application is owned by the head of Sales or the Chief Revenue Officer. Do all those business owners know the expectations for securing their applications? Do they know which security framework the company is following to ensure the right policies and procedures are in place?
The reality is that since all these business applications are owned by different departments, you, as the CISO, may not spend much time inquiring about their security. You might expect that the CFO has security taken care of for the ERP system, while the CFO is trusting IT to set up access, without much consideration for the risk of over-provisioned users that could lead to potential fraud.
When you talk to your board about enterprise security posture, there is an expectation that this means everything—all infrastructure, data, and applications. Effective Application Access Governance (AAG) means you have strong controls over who has access to what within these applications, and how that access is managed, so you can limit your organization’s exposure to issues like fraud and failed audits.
Don’t fall into the trap of focusing so much on the external threats that you lose sight of the internal threats; they are just as real. Organizations lose 5% of their revenue to fraud each year, and the average fraud loss per case is $1.7M, according to the Association of Certified Fraud Examiners. To achieve true enterprise security, you need the right balance and mitigation of both internal and external threats.
Best practices for securing your business applications
The security doughnut illustrates a common gap in enterprise security posture. As a CISO, you can close that gap by working with business application owners to review risk and apply strong controls. A solid foundation starts with putting IT General Controls (ITGCs) in place and enforcing least privilege access—just as you would when protecting against external threats.
Here’s where your focus should be:
1. Analyze Segregation of Duties (SoD) risk
To enforce least privilege, identify SoD risks. That is, the combination of tasks in the application that would cause a financial risk if done by one person, like the ability to create a vendor and pay that vendor. Make sure that no user can perform that action without a process control in place or a separate user to approve that workflow. Make sure you are analyzing access risk at the lowest securable object or permission level to reduce false SoD positives and improve accuracy.
2. Review administrative access (elevated privileges)
Regularly reviewing who has administrative access in your business applications helps ensure that users with elevated privileges have the appropriate authorization. Make sure access is still necessary and tightly controlled to reduce the risk of unauthorized changes to system settings or access to sensitive data.
3. Periodically review user access
Access needs change over time. As users change roles or gain new permissions, it is common for them to become over-provisioned. Conducting regular User Access Reviews (UARs) ensures that permissions align with current job responsibilities and helps prevent privilege creep.
4. Track changes to critical data
Monitoring changes to sensitive or high-value data is key to maintaining data integrity. Logging these changes helps support forensic investigations in case of unauthorized access or accidental changes. If an unauthorized modification occurs, you can quickly trace the source, ensuring accountability and quick remediation.
5. Prioritize security during a system change
Security is often overlooked during an ERP implementation or upgrade. When deadlines surface and the pressure is on, the focus can shift to “let’s just get this system working”. This leads to costly mistakes and prolonged risk exposure that could have been avoided from the day the system went live. When your organization kicks off the implementation or upgrade of a critical business application, make sure you dedicate time to properly design, develop, and test the security aspects.
Automated Application Access Governance strengthens management and reduces risk
Weak access controls can leave organizations vulnerable to insider threats. Managing access manually is time-consuming and error-prone, leading to mistakes and potential security risks.
Automated AAG makes it easier to control and secure access to data across your critical business applications. For example, organizations can run automated checks on user access for SoD and sensitive access risks across multiple applications, quickly spotting conflicts within seconds instead of days.
With automated AAG solutions from Fastpath, now part of Delinea, organizations can streamline access control and reduce risk quickly and efficiently.
Want to read more about the benefits of automated controls? Our whitepaper explains it all.
Download the whitepaper: Automating Your Control Environment.



