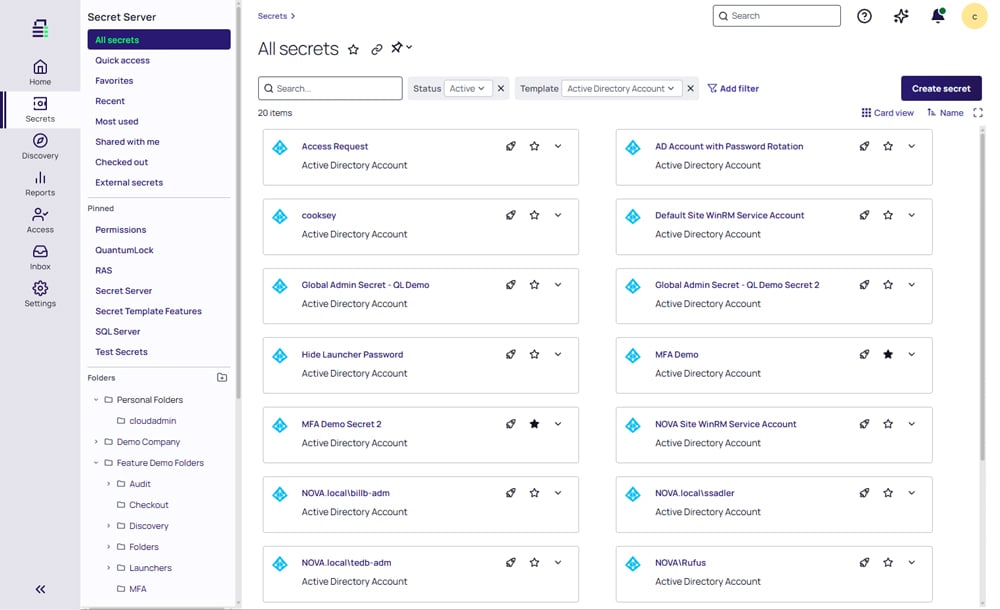
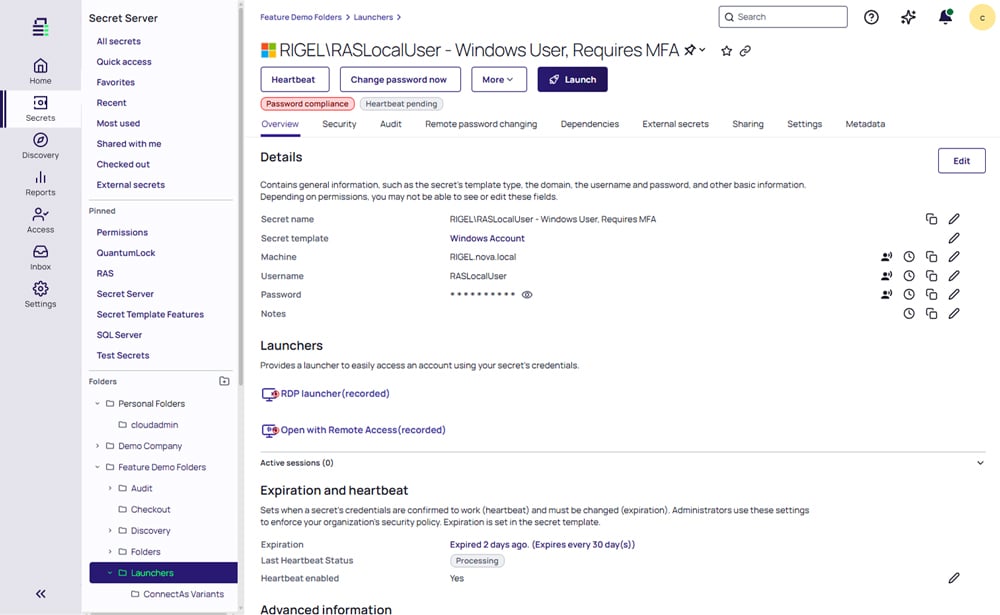
Secret Server
Quickly identify, secure, manage, monitor, and audit privileged accounts in a fully featured, enterprise-grade Privileged Access Management vault that’s powerful, flexible, and easy to use.

Environments are getting more complex and harder to manage while cyber criminals are getting smarter, faster, and more focused on privileged access.
Reduce risk by seamlessly identifying, securing, monitoring and managing privileged account access with a full audit trail for fast proof of compliance.

Powerful Privileged Access Management made easy
Secret Server provides an easy-to-use enterprise-grade vault that identifies and secures every AI, machine, service, application, admin, and root account. With built-in automation for discovery, password rotation, and session monitoring, organizations reduce risk, boost productivity, and scale seamlessly without costly long-term professional services.
This fully featured enterprise-grade vault takes security, efficiency, and usability to the next level.
Encrypted vault
Comprehensive discovery
Automated credential management
Advanced session monitoring
Resiliency
Centralized control

Secret Server, the foundation of the Delinea Platform
- Comprehensive visibility
- Actionable insights
- Scalable controls
- Cost-effective power
What's trending in identity security
Don’t wait to extend and modernize your identity security. Reduce risk, eliminate silos, and scale with confidence.
Download the whitepaper
From mitigating data breach risks to enhancing compliance, these organizations share how Delinea’s Privileged Access Management (PAM) solutions addressed their pain points and delivered both financial and operational returns.
Download the report
Whether you’re new to PAM or updating an existing program, this guide helps you align privilege security with business needs—without getting bogged down in complexity.
Download the eBook