Manage machine identities: The hidden privileged access layer you need to manage
Why are machine identities becoming the majority of “things with access”?
Every automation, integration, and workload needs a way to authenticate and the right permissions to act. That quiet requirement has created a massive population of machine identities, also called non-human identities (NHIs): service accounts, service principals, workload roles, OAuth apps, AI agents, and IAM roles. Machine identities authenticate using credentials like access keys, secrets, and tokens.
Many of these identities hold privileges equal to or greater than human admins because they’re non-interactive, grow fast, rotate rarely, and live long. That makes them a hidden layer of privileged access that often goes unmanaged.
Why is Delinea investing in machine identity capabilities?
Machine identities have become foundational to modern infrastructure, and privileged access accumulates around them.
These machine identities aren’t people; however, they behave like users in your environment by authenticating, requesting access, executing actions, and accumulating privileges across systems, often at greater scale and speed.
Managing machine identity risk isn’t about counting objects. It’s about managing the credentials that give them power: API keys, tokens, certificates, SSH keys, and secrets scattered across cloud stores and vaults.
This sprawl creates familiar risks: outdated credentials, unclear ownership, and privilege creep.
That’s why Delinea is focused on turning machine identity risk into something you can actually manage through visibility, posture, and control across vaulting, rotation, cleanup, and governance.
Where do machine identities actually live?
Machine identities are everywhere software runs and access is granted.
-
In Microsoft environments, you’ll see them in Entra/Azure as app registrations, service principals, and enterprise apps.
-
In AWS, they appear as local accounts and IAM roles used by workloads and automation, plus the access keys and secrets those workloads still rely on in many environments.
-
On-prem, Active Directory service accounts still support long-running tasks.
The takeaway: you can’t manage machine identities in isolation. A real solution spans identity creation, permission assignment, and where credentials are stored.
Why are machine identities a privileged-risk multiplier?
In a nutshell? A lack of visibility, growing complexity, and identity sprawl turn machine identities into a privileged-risk multiplier.
Machine identities can act and be acted on. That means the impact of compromise goes both ways.
If a machine identity has broad permissions and is reused or accessed by automation, one weak spot can expose everything it touches, especially if the credentials are shared, rarely rotated, or no longer monitored.
The goal isn’t to lock down every machine identity. It’s to consistently find the ones that carry the most risk and reduce their access over time.
What does a practical machine identity program look like?
The most effective approach is simple and repeatable:
Visibility → Posture → Control
-
Visibility into machine identities, the credentials they use, their owners, and dependent systems.
-
Posture assessment of risk, including permissions, usage patterns, misconfigurations, and signs of exposure.
-
Control with context by vaulting and governing credentials, rotating them as needed, disabling stale access, and enforcing least privilege.
Which posture checks reduce risk fastest?
Start with the checks that lead straight to action:
-
Administrative and shadow machine (non-human) identities
These carry the biggest blast radius. High privilege plus weak governance is where compromise turns into impact fast. -
Stale machine identities
Identities that haven’t been used recently are often safe candidates to disable once you confirm dependencies. -
Over-privileged machine identities
Permissions tend to accumulate over time. Prioritize identities with broad roles, wildcard policies, or access that exceeds their current function. -
Unvaulted machine identities
Credentials that aren’t centrally stored and governed, especially those living in cloud stores, CI/CD pipelines, code, or config. These unvaulted machine identities are harder to audit and easier to lose control of. -
Non-rotated machine identities
Long-lived keys, secrets, and certificates that haven’t rotated on a predictable schedule increase exposure time and make compromise harder to contain.
How do you fix machine identity risk without breaking production?
This is where many programs get stuck. Machine identities are tied to live workloads, where mistakes can cause downtime.
The key is context: know what a credential is, where it’s used, and what depends on it.
A safe path forward:
-
Inform and route first—don’t make security the bottleneck.
-
Vault and govern high-impact credentials—enable consistent auditing and rotation.
-
Rotate and disable carefully, starting with the safest targets.
-
Refactor access over time—don’t try to fix everything at once.
-
Upgrade authentication methods to reduce credential risk where you can.
How Delinea helps secure machine identities
Delinea helps teams move from finding risks to fixing them using the same practical flow: Visibility ->Posture -> Control.
1) Visibility
Machine identities, credentials, and operational context
Delinea expands visibility across platforms and maps each identity to the secrets and credentials it uses, along with context like ownership and dependencies that determine what you can change safely.
-
In Microsoft Entra/Azure, Delinea discovers app registrations, service principals, and enterprise apps, and with their associated credentials. It flags stale, unvaulted, or inactive identities.
-
In AWS, Delinea discovers secrets in Secrets Manager and highlights metadata like last use, age, and change history to help teams spot unmanaged credentials.
-
In Active Directory, Delinea discovers service accounts and maps their dependencies to IIS, scheduled tasks, and services—so you can rotate credentials without breaking anything.
-
Route issues to the right team: Machine identity programs stall when security findings land in a generic queue. Delinea helps map ownership, so posture issues get routed to the teams responsible for the workloads they affect while keeping accountability clear and response time short.
The goal isn’t just inventory. It’s operational context: what the identity does, how it authenticates, and what relies on it.
2) Posture
Prioritize the issues that move risk the fastest
You don’t need 100 checks. You need the ones that surface what matters, like misconfigurations and exposure patterns that drive real risk reduction.
Delinea focuses on the patterns that consistently lead to risk:
-
High-privilege, administrative, and shadow machine identities
-
Machine identities that aren’t vaulted
-
Inactive or unused identities
-
Overprivileged identities
-
Non-rotated machine identities
To manage all this as a program, you need centralized visibility. The Non-Human Identities Dashboard gives teams a single place to track growth, risk, and improvement. It surfaces stale, over-permissioned, orphaned, and policy-violating identities, along with unusual activity or usage drift.
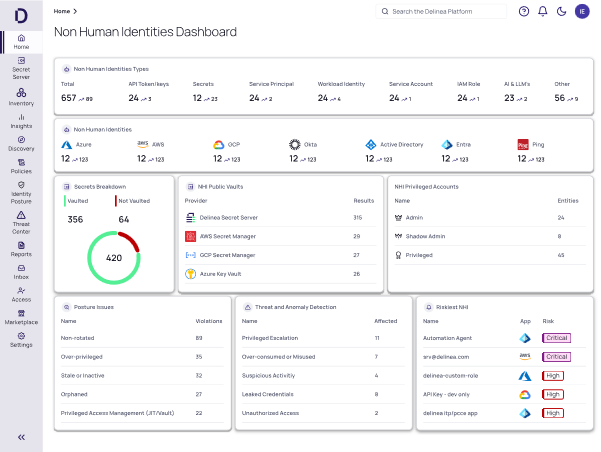
3) Control
Close the loop safely
Identifying risk isn’t enough. You need a production-safe way to resolve it.
With Secret Server, your teams can:
-
Vault high-impact credentials from Active Directory and cloud
-
Rotate credentials manually or automatically using native workflows
-
Disable or retire credentials after validating they’re no longer needed
Remediation is production-safe: prioritize based on context, rotate where you know the dependencies, and validate before disabling anything.
What should you do next?
If you don’t know:
-
Where your machine identities are
-
What credentials they use
-
What they can access
Start here:
-
Run the posture checks that map directly to action: high-privilege and machine identities, unvaulted and non-rotated credentials, stale identities, and privilege drift.
-
Work the program the same way every time: discover with context, prioritize what reduces risk fastest, and remediate in safe increments. Do vaulting and rotating first, disabling only after you’ve validated dependencies.
Machine identities now make up a major share of privileged access. The sooner you manage them with the same discipline as human identities, the sooner you close one of the biggest remaining gaps in identity security.
Ready to get started? See how analysts are recognizing Delinea for leading in human and machine identity security:
Get the 2026 NHI Analyst Report Bundle