Fast, unified PAM and Certificate Lifecycle Management
As your enterprise increases the number of connected devices, certificates are a crucial way to authenticate machine identities and authorize their privileged access.
That said, many organizations manage certificates using different workflows and solutions than they use for other machine or human identities in their organization. This splintered approach increases the likelihood that compliance policies won’t be followed correctly and introduces security vulnerabilities. Closing the gaps typically requires development resources with PowerShell skills or expensive professional services.
In this blog, you’ll learn how you can achieve greater visibility and control over certificate management, renewal, and deployment, as well as protect your organization from certificate-related credential theft.
How does certificate-based authentication work?
While tokens are a better fit for providing short-lived or temporary access, certificates are better for high security/zero trust scenarios. For example, remote servers that sit outside the enterprise security perimeter are a good fit for certificate-based protections.
IoT ecosystems need identity systems that work offline, scale, support mutual authentication, and bind identity to hardware. Certificates deliver on all this, making them ideal for securing IoT devices and orchestrating machine identities.
Certificates secure digital communications, ensuring data integrity and building online trust
If your organization handles personally identifiable information (PII), personal health information (PHI), credit card numbers, and other sensitive data, you’re bound by regulatory requirements to have valid certificates and ongoing certificate governance policies.
- A PKI (Public Key Infrastructure) certificate is a digital document that cryptographically binds a public key to a specific identity and is issued and managed by a trusted authority called a Certificate Authority (CA). These certificates are essential for encrypting data as it’s shared across networks, and confirming identity for general use like web browsing (SSL/TLS) and secure email.
- A private certificate is used to secure internal communications, authenticate users and devices, and manage infrastructure like network devices and servers. Certificates from private CAs offer greater security but must be manually configured to be trusted on the devices within your organization.
With mutual certificate authentication, network devices and servers positively verify each other. Some systems will issue a certificate to each machine uniquely. Sometimes certificates are shared across multiple machines for a load-balanced application.
How Certificate Lifecycle Management (CLM) creates opportunities for bad actors
After you’ve purchased and configured certificates, you need to manage their operations and lifecycles, as certificates expire and must be renewed.
Accessing and managing certificates requires credentials (keys) that unlock privileged access. This process is potentially time-consuming and also increases risk. Credentials for certificates must be shared between applications and teams, creating a potential window for compromise.
Certificate lifespans are shrinking, which means more potential points of failure. The lifespan of TLS/SSL certificates is now just 47 days, so the operational burden isn’t just a yearly nuisance but a near-continuous burden. To avoid unexpected certificate expiration, which could lead to compliance fines or service outages, both certificate and key management must shift from manual work to secure, policy-driven automation.
Poor certificate management exposes vulnerabilities that attackers exploit
Methods of certificate-based attacks include:
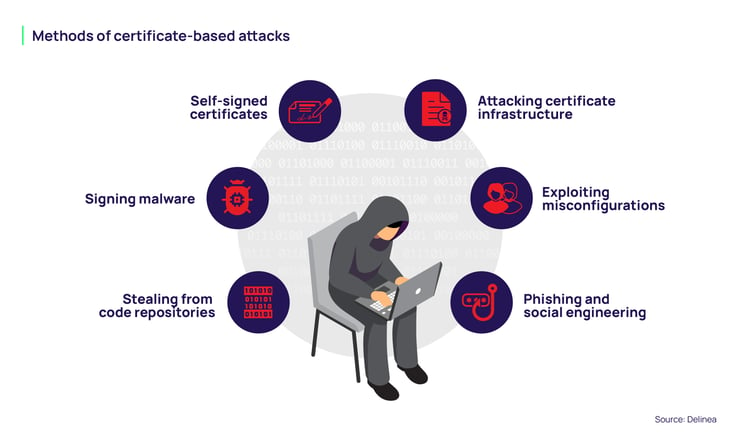
- Attacking certificate infrastructure: Vulnerabilities in the Certificate Authority or its management can allow attackers to create fraudulent certificates. Compromising the root CA can lead to the creation of "golden certificates" to impersonate any user in the domain.
- Exploiting misconfigurations: Improperly configured certificates can enable privilege escalation or lateral movement, as attackers can abuse them to assume the identity of a more privileged user or service.
- Phishing and social engineering: Attackers can create fake websites and obtain certificates for them to appear legitimate, tricking users into providing their credentials.
- Stealing from code repositories: TLS/SSL certificates are sometimes accidentally exposed on public code hosting sites like GitHub, which can then be used by attackers to access private resources.
- Signing malware: Attackers can sign malicious software with stolen certificates to bypass security measures and trick users or security tools into believing the malware is legitimate.
- Self-signed certificates: A self-signed certificate is created without validation from a trusted third-party Certificate Authority. Attackers may introduce their own self-signed certificates to make rogue devices appear legitimate.
The primary risk in certificate-based authentication is poor key management
Keys that unlock certificate-based authentication should be unique. When the same key is used for multiple certificates, the compromise of one device effectively compromises every device sharing that certificate. This dramatically expands the potential blast radius of an attack.
If a certificate key is exposed due to malware, insecure storage, or device loss, it could lead to unauthorized access. Keys should be rotated regularly to limit the time any compromised key can be used by an attacker.
How to protect certificates from theft and exploitation
A digital vault, like Secret Server, is a central, secure storage system that reduces the risk of compromised certificates and keys.
Through Secret Server, you can govern certificates and the keys that unlock them in the same way you address any type of secret that prevents unauthorized access, such as passwords.
As an end-to-end solution, Delinea integrates seamlessly with leading Certificate Lifecycle Management (CLM) providers Sectigo and Keyfactor, minimizing the risk of expired certificates and service disruptions.
How it works:
These CLM solutions automatically retrieve credentials required for certificate operations from Secret Server.
- Rotated keys in Secret Server are automatically updated in the CLM, removing any chance that credential rotation breaks communication.
- Keys are not exposed to operations teams or within the CLM, reducing the risk of theft or reuse.
- Should you discover that certificate credentials are compromised, Secret Server enables credential rotation that can be triggered either on-demand or based on pre-configured policies, rendering compromised credentials unusable by bad actors.
- The solution makes audit and compliance more efficient by increasing visibility of certificate management and streamlining reporting of your cryptographic asset inventory.
In addition to vaulting and managing keys, the integrations also automate Certificate Lifecycle Management.
Manage all machine identities in one place
As the number of machine identities grows and becomes more diverse, you should be able to manage and secure them all from a common solution. Mandatory prerequisites for a unified solution are consistent policies and flexibility to adapt to different workflows.
The combined solution of Delinea, plus these preferred CLM vendors, delivers faster time to value and real-world agility compared with monolithic certificate-based authorization solutions that are rigid and complex.
With Delinea, all certificate and key lifecycle operations are subject to the same governance and compliance policies as all other privileged accounts across your IT environment. Plus, IT operations staff can go to one place for all secrets management workflows including lifecycle management and reporting. That helps eliminate redundant tools and spend. Especially if you’re a Managed Service Provider managing certificates and keys for hundreds of clients, that can lead to tremendous time savings.
Integrations between Delinea and Keyfactor or Sectigo don’t require heavy professional service dependencies, PowerShell scripting, or custom workflows. They can be deployed on-premise or in the cloud and scale as your use of certificate-based authentication increases.
You can learn more about Delinea integrations with Keyfactor and Sectigo, and other solutions for certificate management in the Delinea Marketplace.