Credential misuse at scale is now the default
Delinea Labs February 2026 Threat Outlook
In this monthly series, Delinea Labs reviews the identity-related activity that had the greatest operational impact over the previous month. We focus on how attacks unfolded, what failed in real environments, and what those failures signal for the month ahead.
January 2026 didn’t bring a wave of new techniques. Instead, it showed how established identity abuse patterns are becoming routine. Across breaches, ransomware campaigns, and vulnerability disclosures, attackers didn’t break in. They authenticated, automated, and waited to strike.
From compromised non-human identities to large-scale credential harvesting fueling ransomware, January’s incidents shared a consistent characteristic: identity misuse occurred long before impact and largely went undetected.
Here’s Delinea Labs’ outlook for February.
The big theme: access is no longer a gate, but a path to compromise
January continued a shift that has been unfolding steadily over the past several years.
For many attackers, authentication has replaced exploitation as the most reliable way into production systems
Adversaries are increasingly bypassing endpoints and exploits entirely, relying instead on valid credentials, OAuth tokens, and service accounts that already have access to sensitive systems.
The n8n automation platform compromise illustrated this dynamic. By distributing malicious community nodes, attackers were able to harvest OAuth tokens and embedded secrets, allowing them to pivot laterally across connected SaaS platforms without touching user accounts. By operating through trusted automation workflows, they avoided traditional identity monitoring entirely.
At the same time, activity tied to the OpenClaw ecosystem, including ClawDBot and MoltBolt, highlighted how large-scale credential harvesting at scale continues to supply ransomware groups and attackers with valid access long after original compromise. Credentials were collected and reused weeks or months later, often in environments where the initial exposure had gone unnoticed.
What we’re seeing at Delinea Labs: non-human identities move to the foreground
Across January’s investigations and disclosures, several consistent trends emerged:
-
Automation identities as primary attack paths: Compromised automation platforms acted as identity brokers, granting access across SaaS and cloud services without triggering user-centric controls.
-
Service accounts bypass MFA by default: Non-human identities continued to authenticate without interactive safeguards, creating blind spots where attackers could operate freely.
-
Credential harvesting fuels delayed impact: Stolen credentials collected at scale were leveraged weeks or months later, enabling ransomware, extortion, and data theft long after initial compromise.
-
Ransomware remains identity-first: Groups like Qilin, Akira, and Sinobi relied primarily on valid credentials for initial access and persistence, authenticating well before encryption or extortion activity appeared.
Identity infrastructure is under pressure—and monitoring isn’t keeping up
January also saw continued disclosure of vulnerabilities affecting identity systems. Of the 1,870 CVEs reported industry-wide, 360 were identity-related, with 16 directly impacting identity providers, access management platforms, and authentication services.
While these vulnerabilities represented a small fraction of total disclosures, their impact was disproportionate. Flaws in token validation, trust relationships, and authentication logic enable attackers to bypass controls and pivot across environments once access is established.
Notable examples included:
-
A critical n8n pre-authentication takeover vulnerability that allowed attackers to run workflows and access secrets without credentials.
-
A JWT signature bypass in Fleet MDM that enabled unauthorized device enrollment under arbitrary cloud identities.
-
A high-severity Microsoft Entra ID privilege escalation flaw that expanded blast radius across tenants.
These vulnerabilities matter because credential theft rarely occurs in isolation. Once attackers hold valid identities, weaknesses in validation and authorization determine how far—and how quietly—that access can spread.
Ransomware reporting in January reflected a similar pattern. While Qilin, Akira, and Sinobi accounted for roughly one-third of reported incidents, more than half were attributed across smaller groups.
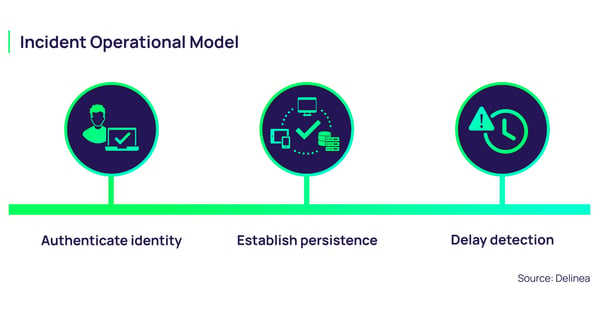
Regardless of size, the operational model was the same: authenticate successfully, establish persistence, and delay detection until data theft or extortion forced discovery.
In most cases, the activity was logged. It just didn’t look suspicious.
What enterprises should prepare for next
Identity-driven attacks are unlikely to slow. Delinea Labs expects continued targeting of non-human identities, deeper abuse of automation platforms, expanded social engineering against SSO workflows, and increased exploitation of weaknesses in identity infrastructure itself.
What organizations should prioritize:
-
Continuous identity threat detection across users, tokens, and service accounts.
-
Lifecycle governance for both human and machine identities to eliminate orphaned access.
-
Real-time monitoring of privileged and automated activity.
-
Centralized vaulting, rotation, and scope reduction for secrets and API keys.
-
Policy-driven authorization and session validation beyond initial login.
Identity security has moved beyond login events. Control, visibility, and governance now determine how quickly access is contained or how long credential misuse goes unnoticed.
Check out the Delinea Platform powered by Iris AI to learn how you can strengthen identity security without sacrificing speed or visibility.