Considerations for Operational Technology Cybersecurity
Operational Technology (OT) refers to the hardware and software used to change, monitor, or control the enterprise's physical devices, processes, and events. Unlike traditional Information Technology (IT) systems, OT systems directly impact the physical world. This unique characteristic of OT brings additional cybersecurity considerations not typically present in conventional IT security architectures.
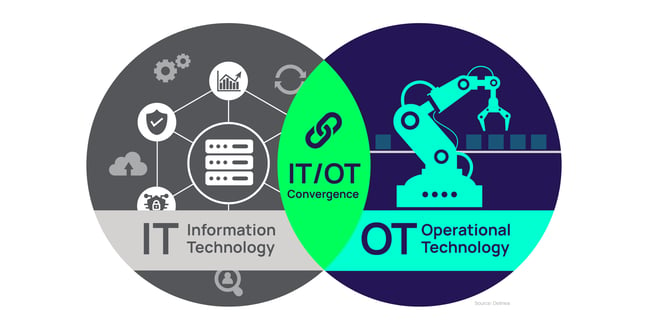
The convergence of IT and OT
Historically, IT and Operational Technology (OT) have operated in separate silos, each with its own set of protocols, standards, and cybersecurity measures. However, these two domains are increasingly converging with the advent of the Industrial Internet of Things (IIoT). While beneficial in terms of increased efficiency and data-driven decision-making, this convergence also exposes OT systems to the same cyber threats that IT systems face.
Unique Cybersecurity Considerations for OT
Real-time requirements
Operational Technology systems often operate in real time and cannot afford delays. A delay in an OT system could lead to significant operational issues or even safety hazards. Therefore, OT cybersecurity measures that introduce latency, such as multi-factor authentication, just-in-time access request workflows, and session activity monitoring, may not be suitable for OT environments.
Note that the impact of these features on system performance can vary based on the specific PAM solution and how it's configured. Therefore, it's crucial to thoroughly test any PAM solution in a real-time environment to ensure it meets performance requirements while still providing necessary security controls.
Legacy systems and connectivity
Many Operational Technology systems are still old in the tooth. They're proprietary and customized to meet the needs of longevity and resilience under harsh conditions. Cybersecurity was not a high-priority consideration for legacy OT systems, so they lack resilience against contemporary OT cybersecurity threats, resulting in high risk.
They may lack basic security capabilities such as encryption, authentication, and Multi-Factor Authentication (MFA.) Modernizing these systems presents significant challenges in terms of cost, operational disruptions, and compatibility issues. People with knowledge and skills may not be available, making understanding the design and the code impossible.
With the increasing integration of these systems into IT networks and, occasionally, the internet, their susceptibility to cyber threats is amplified. While beneficial for operational efficiency, this connectivity inadvertently expands their attack surface, thereby escalating their vulnerability.
Some examples of unique security challenges include:
- Outdated Hardware and Software: Obsolete hardware and software introduce significant security challenges due mainly to incompatibility with modern off-the-shelf security solutions and best practices. This exposes legacy OT systems to unauthorized surveillance, data breaches, ransomware attacks, and potential manipulation.
- Lack of Encryption: Encryption is crucial for safeguarding sensitive data and communications. Nonetheless, older OT systems might not have the capability to support encryption, which exposes them to attacks that could jeopardize the confidentiality and integrity of data.
- Insecure Communication Protocols: Legacy OT systems may use insecure communication protocols that attackers can exploit. For example, Modbus, a widely used communication protocol in legacy OT systems, does not include authentication or encryption, making it vulnerable to attacks.
- Limited Ability to Implement Cybersecurity Controls: Traditional OT systems frequently have a restricted capacity to apply cybersecurity measures. For example, they might have been provided before the importance of cybersecurity was recognized and managed by OEMs, complicating their security.
- Third-Party Remote Connections: Older OT systems might support remote connections from third parties to manage OT devices linked to an internal network. Intruders can target a network established by a vendor and exploit it to contaminate other devices.
- Lack of Security Awareness: Operators and technicians who manage legacy OT systems may lack security awareness and training, making them vulnerable to social engineering attacks.
- Embedded or Easy-to-Guess Credentials: Certain OT devices, such as those in the IoT category, might possess inherent or predictable passwords, along with other potential design shortcomings.
 Safety and reliability
Safety and reliability
In Operational Technology environments, the primary focus is maintaining the safety and reliability of the physical processes they control. This is a significant departure from traditional IT environments, where the focus is often on the confidentiality and integrity of data.
- Safety: OT systems control physical processes that can have real-world consequences if they malfunction. For example, in a power plant, a failure in the control system could lead to a shutdown or even a catastrophic event. Therefore, ensuring the safety of these systems is paramount.
- Reliability: OT systems must be available and function correctly to ensure the smooth operation of physical processes. Any downtime can lead to significant operational disruptions and financial losses.
In contrast, in OT environments, confidentiality (preventing unauthorized access to information) and integrity (ensuring that data remains accurate and unaltered) often take a backseat. While these elements are significant, they usually don't hold as much weight as safety and reliability.
This order of priority can affect the implementation of cybersecurity measures. A cybersecurity action that safeguards data (boosting confidentiality and integrity) but jeopardizes the dependability of an OT system might not be deemed suitable. For instance, a security patch could rectify a known vulnerability (improving integrity), but you might consider it unsuitable if it results in system instability (undermining reliability).
While many cybersecurity best practices and frameworks focus on traditional IT environments, OT can also benefit. For example, OWASP Top 10 addresses web application cybersecurity concerns such as injection, broken authentication, sensitive data exposure, and security misconfigurations, which are common vulnerabilities that can also be found in OT environments. OWASP also has a separate list for the Internet of Things (IoT), which is often a significant component of OT environments.
Cybersecurity strategies in OT environments must be carefully designed to balance the need for safety and reliability with the need for data confidentiality and integrity
Thus, cybersecurity strategies in OT environments need to be carefully designed to balance the need for safety and reliability with the need for data confidentiality and integrity. This often requires a different approach than traditional IT security, focusing more on minimizing disruptions to physical processes. It's a delicate balancing act that requires deep knowledge of operational processes and potential cyber threats.
Securing OT environments requires a different approach compared to traditional information technology security. It requires understanding OT systems' unique characteristics and requirements, as well as designing cybersecurity measures that can protect them without compromising their operation.
As IT and OT continue to converge, the importance of OT cybersecurity will only increase. The use of encryption is crucial for safeguarding sensitive data and communications. Nonetheless, older OT systems might not have the capability to support encryption, which exposes them to attacks that could jeopardize the confidentiality and integrity of data.