Integrating privileged account management into DevOps

Tucker Hall
By 2021, security practices will be embedded in 80% of rapid development teams. That’s a rapid increase from 15% in 2017, according to Gartner. Hence the term, “DevSecOps.”
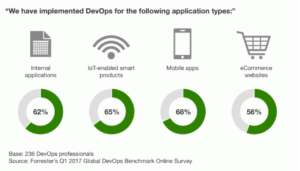
Just a few years ago, DevOps was still a new concept, only implemented by cutting-edge tech teams pushing out dozens or hundreds of software updates per day. These days, at least half of IT organizations are currently using DevOps, according to Forrester Research. Among DevOps organizations, 70% use DevOps to build and maintain mission-critical applications.
DevOps is used for all types of application development
With DevOps on the rise, the old ways of managing security tools and controls are no longer an option. Traditionally, integrating security into a software development lifecycle required handoffs and wait time. Today, security teams must meet expectations for speed and ease of use. They are adapting security to the development process, breaking security out of its silo.
What does that mean for security teams responsible for privilege access management?
The rapid, iterative DevOps workflow often exposes many security vulnerabilities directly tied to privilege management.
- Many tool configurations, scripts, code files, test builds, and production builds exchange information with other services and accounts, APIs, or databases, which require credentials to authenticate. Developers may embed hardcoded keys or credentials in a file somewhere in an application’s environment, which then becomes a security vulnerability.
- During build, developers may also store credentials in a repository such as GitHub, forget about them, and then commit them to production. These exposed credentials are a potential vulnerability that opens a back door into sensitive systems.
- DevOps teams often use open source code within the production process. Grabbing and integrating code found in a repository like GitHub could mean picking up someone else’s bad practices and integrating hardcoded or shared credentials into an application.
- In a DevOps team, many people need on-demand access to source code, tools, test servers, production builds, and more to administer systems and debug production issues. It’s common to share private keys and credentials for immediate access, which increases the risk of insider threats, either malicious or accidental.
- DevOps teams must build products and features compatible with different sized environments, from dozens, hundreds or thousands of servers using different types of hardware at multiple locations, including cloud, multi-cloud, and hybrid-cloud. Administrative privileges are used by the configuration management and orchestration systems that continually spin up new servers, install software and make configuration changes These accounts must be discovered, protected, controlled, and managed.
- The Continuous Integration (CI) tool chain DevOps teams employ involves a changing set of fragmented, often open-source tools, and constant integration of new tools and applications into the process. Organizations need to allow developers to choose DevOps tools and run processes without having local admin privileges.
Worried yet?
If you are responsible for keeping credentials safe at your organization, you must be aware of the potential security gaps in a DevOps environment and make sure you have the privilege management tools and practices in place to support the velocity and scale DevOps teams demand.
Extending enterprise-grade privilege management to the DevOps environment closes a blind spot that security and PAM teams have had in their privilege management policies.
Manage DevOps secrets safely